The landscape of cybersecurity is ever-evolving, presenting new challenges and requiring innovative solutions. 💡
For decades, Virtual Private Networks (VPNs) have been the cornerstone of secure remote access, allowing employees to connect to corporate resources as if they were physically present in the office. 🌐
However, with the rise of cloud computing, hybrid work models, and an increasing threat surface, the limitations of traditional VPNs are becoming more apparent. 🧐
Enter Zero Trust Network Access (ZTNA), a modern approach that challenges the fundamental assumption of trust within a network. 🛡️
This blog post will dive deep into the world of security frameworks, contrasting VPNs with ZTNA, exploring their nuances, benefits, and the implications for compliance and the future of secure access. 🚀
Understanding the Traditional VPN Model
A VPN creates an encrypted tunnel over a public network, allowing users to securely access private network resources. 🔒
Once a user authenticates with a VPN, they are typically granted broad access to the internal network. 🔑
This “connect once, access everything” model made sense when corporate networks were largely on-premises and users were primarily within the office perimeter. 🏢
However, this model also introduces significant security risks. 😱
If an attacker compromises a user’s VPN credentials, they can potentially gain unfettered access to a wide range of sensitive data and systems within the network. 😈
Moreover, managing VPN infrastructure can be complex, especially for large organizations with a globally distributed workforce. 🌍
The VPN’s Role in Compliance 📋
For many years, VPNs were sufficient for meeting various compliance requirements related to data privacy and access control. ✅
Regulations like HIPAA, GDPR, and PCI DSS often mandate secure transmission of sensitive data, and VPNs provided a clear mechanism for achieving this. 📜
However, the evolving regulatory landscape, coupled with the increasing sophistication of cyber threats, has highlighted the need for more granular and adaptive security controls. ⚖️
“Trust but verify” has evolved into “never trust, always verify.”
The Rise of Zero Trust Network Access (ZTNA)
Zero Trust is not a single product but a security philosophy built on the principle of “never trust, always verify.” 💯
ZTNA is a key technology that implements this philosophy by ensuring that no user or device is inherently trusted, regardless of whether they are inside or outside the traditional network perimeter. 🚫
Instead of granting broad network access, ZTNA provides highly granular, context-aware access to specific applications and resources. 🎯
This means that even if an attacker compromises a user’s credentials, their access is limited to only the resources they are explicitly authorized to use, significantly reducing the blast radius of a breach. 🔥
ZTNA platforms authenticate users and devices, verify their security posture, and then establish secure, encrypted connections to specific applications, not the entire network. 🤝
Key Principles of Zero Trust 🗝️
- Verify explicitly: Authenticate and authorize every device and user before granting access, based on all available data points, including user identity, location, device health, and service requested. 🔐
- Least privileged access: Grant users and devices only the minimum access necessary to perform their tasks, and nothing more. This significantly limits potential lateral movement for attackers. 🤏
- Assume breach: Design security with the assumption that breaches will occur. This involves segmenting networks and continuously monitoring for suspicious activity. 🚨
- Micro-segmentation: Break down the network into smaller, isolated segments, with strict controls governing traffic between them. This prevents attackers from easily moving between different parts of the network. 🔬
- Continuous monitoring: Continuously monitor user and device behavior, as well as network traffic, for anomalies that could indicate a threat. 👁️
These principles collectively create a much stronger security posture than traditional perimeter-based approaches. 💪
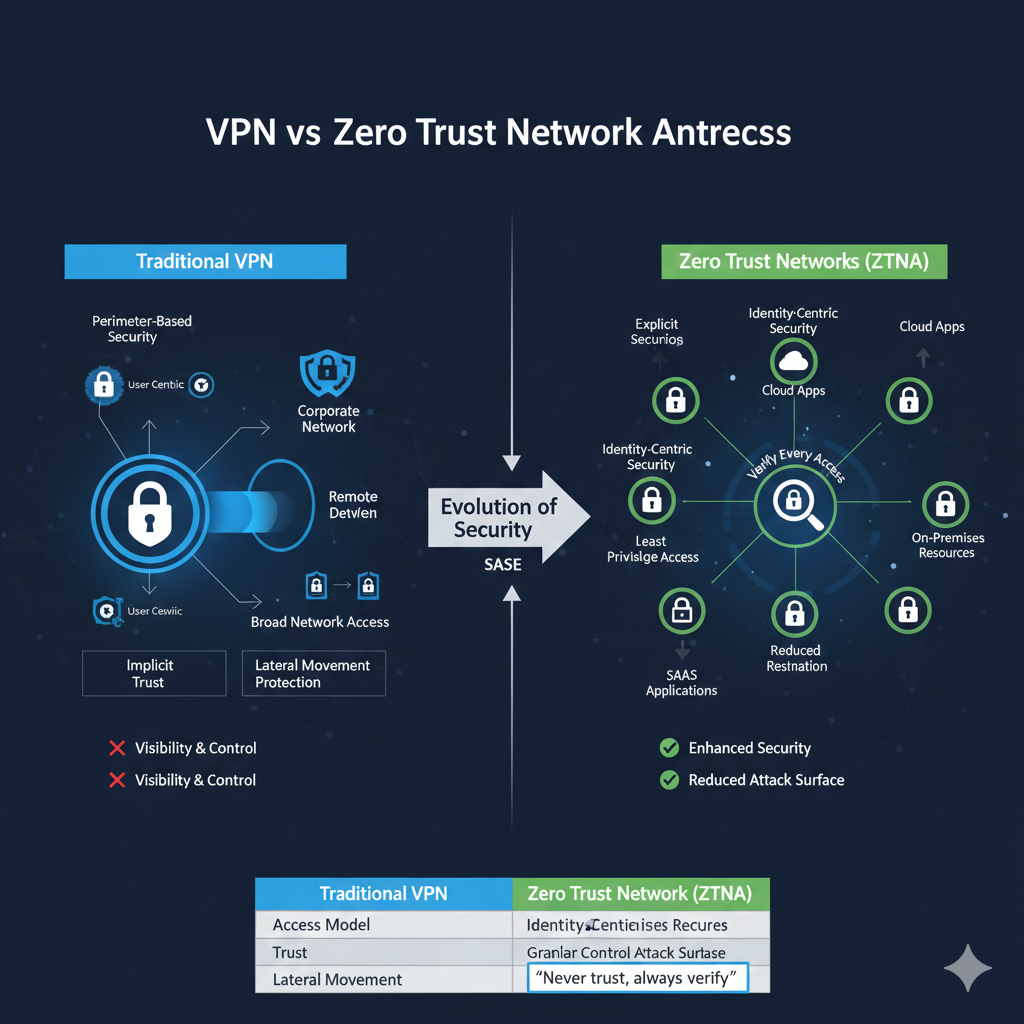
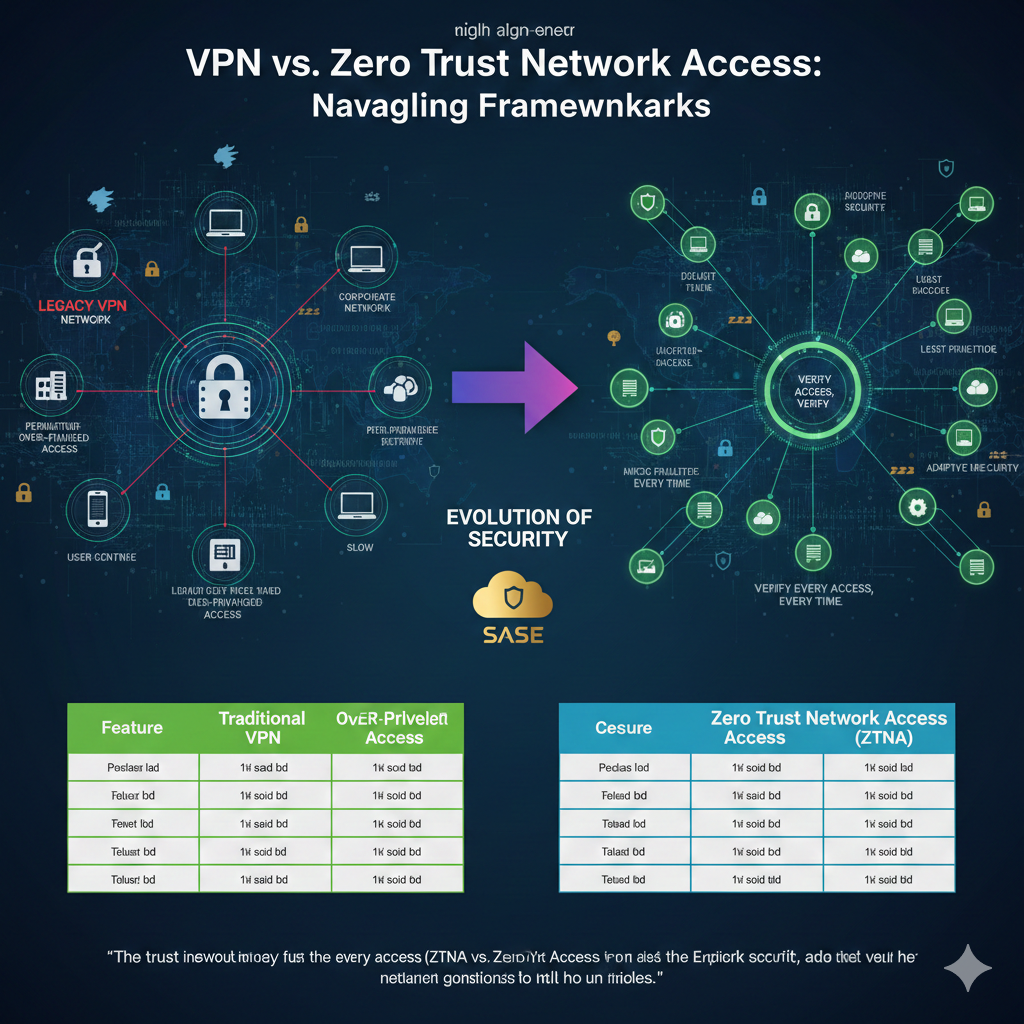
VPN vs. ZTNA: A Comparative Analysis
Let’s break down the core differences between VPNs and ZTNA across several critical dimensions. 📊
| Feature | Traditional VPN | Zero Trust Network Access (ZTNA) |
|---|---|---|
| Access Model | Network-centric, broad access after authentication. | Application-centric, granular access to specific resources. |
| Trust Philosophy | Trusts users and devices once connected to the network. | Never trusts, always verifies every access request. |
| Security Perimeter | Focuses on securing the network perimeter. | Extends protection to every user, device, and application regardless of location. |
| Lateral Movement | High risk of lateral movement if an endpoint is compromised. | Significantly reduces lateral movement by isolating application access. |
| User Experience | Can be slow and complex to manage for remote users. | Often provides a seamless and faster user experience, especially for cloud apps. |
| Scalability | Can be challenging to scale for a large, distributed workforce. | Highly scalable, designed for cloud-native and hybrid environments. |
Security Posture 🛡️
VPNs, by their nature, create a wide-open gateway into the corporate network. 🚪
This “flat network” model allows an attacker who gains access to one part of the network to potentially move freely to other parts. 🚶♂️
ZTNA, conversely, creates a “micro-perimeter” around each application or resource. 🔒
Access is granted on a per-session, per-application basis, and each request is re-evaluated based on real-time context. ⏰
This drastically limits the potential impact of a compromised credential or device. It’s like having a dedicated, secure pathway for each specific application, rather than a single bridge to the entire city. 🌉
User Experience and Performance 🚀
Traditional VPNs can often introduce latency and slow down network performance, especially when backhauling all traffic to a central data center. 🐌
This can be particularly problematic for cloud-based applications, where traffic has to travel an unnecessarily long route. ☁️
ZTNA, being cloud-native in many implementations, routes traffic directly to the applications users need, optimizing performance and providing a smoother user experience. ✨
This direct-to-app access bypasses the latency issues often associated with VPNs. ⚡
Management and Scalability 📈
Managing a VPN infrastructure, especially for large and geographically dispersed organizations, can be a complex and resource-intensive task. 🤯
Configuring access rules, managing client software, and scaling hardware to meet demand can be a significant undertaking. 🛠️
ZTNA solutions, often delivered as a service (SaaS), simplify management considerably. ☁️
They are designed to scale effortlessly with the growth of your organization and the increasing number of remote users and cloud applications. 🌐
This “as a service” model offloads much of the infrastructure management burden from internal IT teams. 🧑💻
Compliance and Regulatory Considerations 📜
While VPNs have historically played a role in compliance, ZTNA offers a more robust and granular approach to meeting modern regulatory requirements. The National Institute of Standards and Technology (NIST), for example, has published guidance on Zero Trust Architecture, recognizing its importance in government and enterprise security. 🏛️
ZTNA’s ability to enforce least privilege access, provide detailed audit trails, and ensure continuous verification aligns perfectly with the principles of data privacy regulations like GDPR, CCPA, and HIPAA. ✅
By limiting access to only what is absolutely necessary, organizations can significantly reduce their risk of non-compliance and data breaches. 📉
The explicit verification and granular access controls inherent in ZTNA are crucial for demonstrating compliance in an increasingly stringent regulatory environment. 🌍
The Evolution to SASE (Secure Access Service Edge) 🌌
The discussion of ZTNA often leads to the broader concept of Secure Access Service Edge (SASE). 🌟
SASE is a cloud-native architecture that converges networking and security functions into a single, integrated platform. 🧩
It combines elements like ZTNA, Firewall-as-a-Service (FWaaS), Secure Web Gateway (SWG), and Cloud Access Security Broker (CASB) into a unified offering. ☁️
ZTNA is a foundational component of SASE, providing the secure, identity-driven access that is central to the SASE vision. 🏗️
By adopting a SASE framework, organizations can simplify their security architecture, improve performance, and enhance their overall security posture in a world where users and applications are everywhere. 🌐
“The network is now the internet, and the perimeter is the identity.”
When to Choose ZTNA Over VPN 🎯
While VPNs still have their place for certain legacy applications or specific use cases, the shift towards ZTNA is becoming increasingly necessary for most modern organizations. 🔄
Here are some scenarios where ZTNA is the clear winner: 🏆
- Hybrid and Remote Workforces: With a significant portion of employees working remotely, ZTNA provides a more secure and efficient way to access cloud and on-premises applications. 🏡
- Cloud-First Strategies: Organizations heavily invested in cloud applications and infrastructure will find ZTNA better suited for securing access to these distributed resources. ☁️
- Third-Party Access: Granting secure, limited access to contractors, partners, or vendors without giving them full network access is a core strength of ZTNA. 🤝
- Advanced Threat Protection: ZTNA’s continuous verification and micro-segmentation capabilities offer superior protection against sophisticated cyber threats, including ransomware and insider threats. 🦠
- Streamlined Compliance: Meeting stringent regulatory requirements becomes easier with ZTNA’s granular control and detailed logging. 📄
Ultimately, the decision to move from VPN to ZTNA is a strategic one that aligns with an organization’s overall digital transformation and cybersecurity goals. 🎯
Implementing ZTNA: A Practical Approach 🛠️
Transitioning to ZTNA doesn’t have to be an all-or-nothing endeavor. Many organizations adopt a phased approach, gradually migrating applications and users to the ZTNA model while maintaining VPNs for legacy systems. 🪜
Key steps in implementing ZTNA include: 👇
- Identify and Classify Applications: Understand which applications are critical and how users access them. 🏷️
- Implement Strong Identity and Access Management (IAM): A robust IAM solution is fundamental to ZTNA, as identity is the new perimeter. Learn more about IAM here. 🧑💻
- Deploy a ZTNA Solution: Choose a vendor that offers a scalable, cloud-native ZTNA platform that integrates with your existing security ecosystem. 🤝
- Define Access Policies: Create granular policies based on user identity, device posture, location, and the specific application being requested. 📝
- Monitor and Iterate: Continuously monitor access patterns, identify anomalies, and refine policies as needed. 📊
The journey to Zero Trust is an ongoing process, but the benefits in terms of enhanced security, improved user experience, and simplified management are well worth the effort. ✨
The Future of Secure Access 🔮
The trend towards Zero Trust and SASE is undeniable. 🚀
As organizations continue to embrace cloud computing, remote work, and a distributed workforce, the traditional perimeter-based security model becomes increasingly obsolete. 🗑️
ZTNA represents a fundamental shift in how we approach network security, moving away from implicit trust and towards explicit verification at every access point. 📍
This paradigm shift is essential for protecting sensitive data, ensuring regulatory compliance, and staying ahead of the evolving threat landscape. 🌐
Embracing ZTNA is not just about adopting a new technology; it’s about adopting a proactive and resilient security posture for the digital age. 💡
“Security is not a product, but a process.”
For further reading on Zero Trust principles, consider exploring NIST Special Publication 800-207, Zero Trust Architecture. 📚
Infographic: Key Differences at a Glance 📊
To help visualize the distinctions, here’s an infographic summarizing the core differences between VPN and ZTNA:
