In today’s interconnected world, cybersecurity is no longer just an IT concern; it’s a fundamental business imperative.
Organizations of all sizes and sectors face an ever-evolving landscape of cyber threats.
To navigate this complexity, many turn to established guidelines and frameworks.
Among the most respected and widely adopted is the National Institute of Standards and Technology (NIST) Cybersecurity Framework (CSF).
The NIST CSF provides a flexible, outcome-driven approach to managing cybersecurity risk.
It’s designed to help organizations understand, assess, prioritize, and communicate their cybersecurity efforts effectively.
While it doesn’t prescribe specific technologies or solutions, it offers a common language and a structured methodology.
Let’s explore the core components that make up this powerful framework, focusing on the latest CSF 2.0 updates.

Videos are added as random thoughts 💭 💭 💭.
The Framework Core: The Heart of the CSF
At the very center of the NIST CSF is the Framework Core.
This is essentially a taxonomy of high-level cybersecurity outcomes.
It’s designed to be intuitive and to act as a translation layer, enabling clear communication between multi-disciplinary teams using simple, non-technical language.
The Core is structured into three parts: Functions, Categories, and Subcategories.
The Six Functions (CSF 2.0)
Previous versions of the CSF featured five core functions: Identify, Protect, Detect, Respond, and Recover.
With the release of CSF 2.0, a crucial new function has been added:
Govern. These six functions organize cybersecurity outcomes at their highest level, providing a comprehensive view of an organization’s cybersecurity risk management.
1. Govern (GV): This new function in CSF 2.0 emphasizes the importance of establishing, communicating, and monitoring the organization’s cybersecurity risk management strategy, expectations, and policy.
It ensures that cybersecurity is integrated into the broader enterprise risk management (ERM) strategy.
This includes understanding organizational context, establishing cybersecurity strategy and supply chain risk management, defining roles and responsibilities, and overseeing policy.
It’s about setting the stage and providing the strategic direction for all other cybersecurity activities.
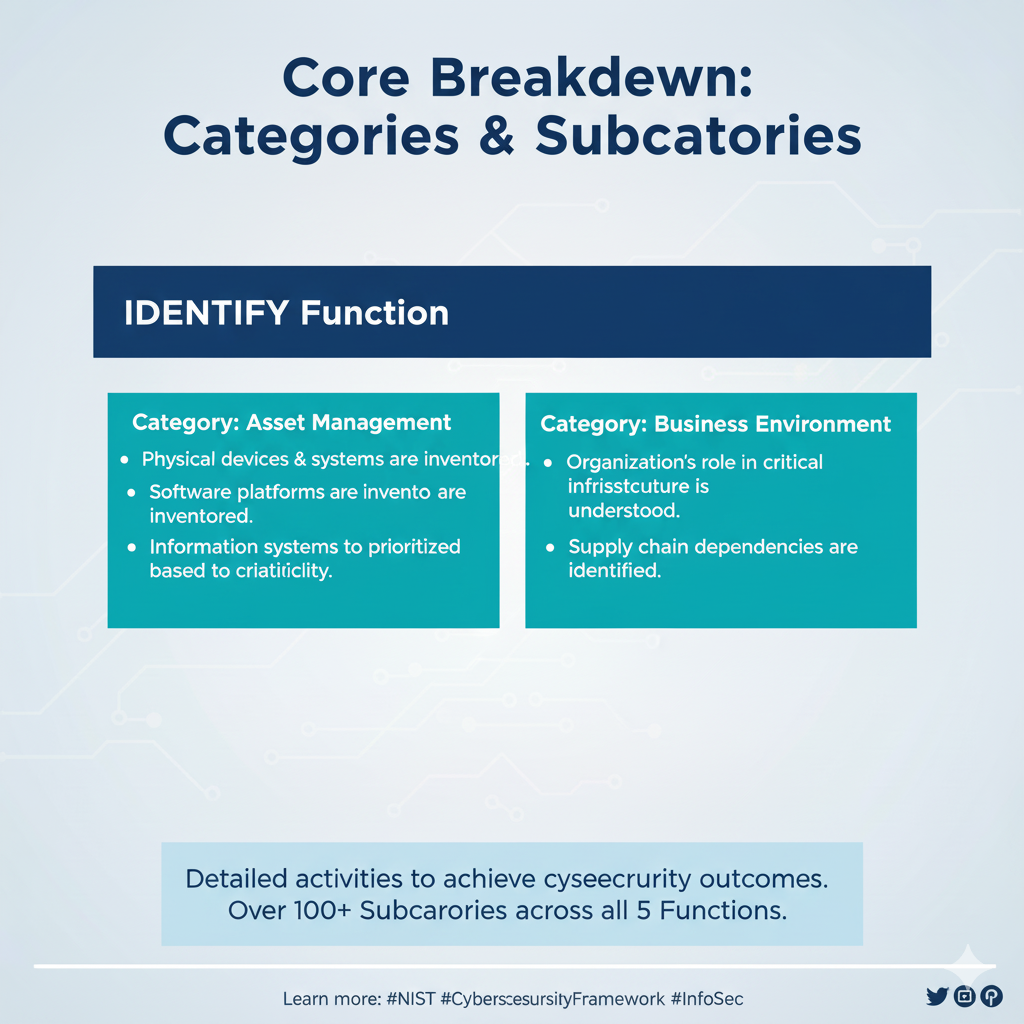
2. Identify (ID): This function focuses on developing an organizational understanding to manage cybersecurity risk to systems, assets, data, and capabilities.
It involves identifying physical and software assets, business environment, governance, risk assessment, and risk management strategy.
Essentially, you can’t protect what you don’t know you have.
3. Protect (PR): Once assets and risks are identified, the Protect function comes into play.
It outlines safeguards to manage the organization’s cybersecurity risks.
This includes implementing appropriate safeguards to ensure the delivery of critical infrastructure services.
Examples include identity management and access control, awareness and training, data security, information protection processes and procedures, maintenance, and protective technology.
It’s all about preventing a cybersecurity event from occurring or limiting its impact.
4. Detect (DE): This function is all about identifying the occurrence of a cybersecurity event.
It enables timely discovery of cybersecurity incidents.
Activities include anomalies and events monitoring, security continuous monitoring, and detection processes.
Think of it as your organization’s early warning system, constantly scanning for unusual activity.
5. Respond (RS): When a cybersecurity event is detected, the Respond function guides appropriate actions to take.
It focuses on containing the impact of a detected cybersecurity incident.
This involves response planning, communications, analysis, mitigation, and improvements.
A swift and effective response can significantly reduce damage.
6. Recover (RC): The final function deals with resilience and restoration.
It outlines activities to maintain plans for resilience and to restore any capabilities or services that were impaired due to a cybersecurity incident.
This includes recovery planning, improvements, and communications.
The goal is to return to normal operations as quickly as possible after an incident.
Categories and Subcategories
Beneath these high-level functions are Categories, which are subdivisions of a function.
These categories cover the breadth of cybersecurity objectives for an organization without being overly detailed.
They span cyber, physical, and personnel aspects, always with a focus on business outcomes.
The deepest level of abstraction in the Core is the Subcategories.
These are outcome-driven statements that provide considerations for creating or improving a cybersecurity program.
There are 108 Subcategories in CSF 1.1, and a similar structure exists in CSF 2.0.
Because the Framework is outcome-driven, it doesn’t dictate how an organization must achieve these outcomes, allowing for risk-based implementations tailored to specific organizational needs.
Each Subcategory is supported by Informative References.
These are broad references that are more technical than the Framework itself, pointing to existing standards, guidelines, and practices that can help an organization achieve the desired outcome.
Organizations can choose to use some, none, or all of these references based on their specific context and requirements.
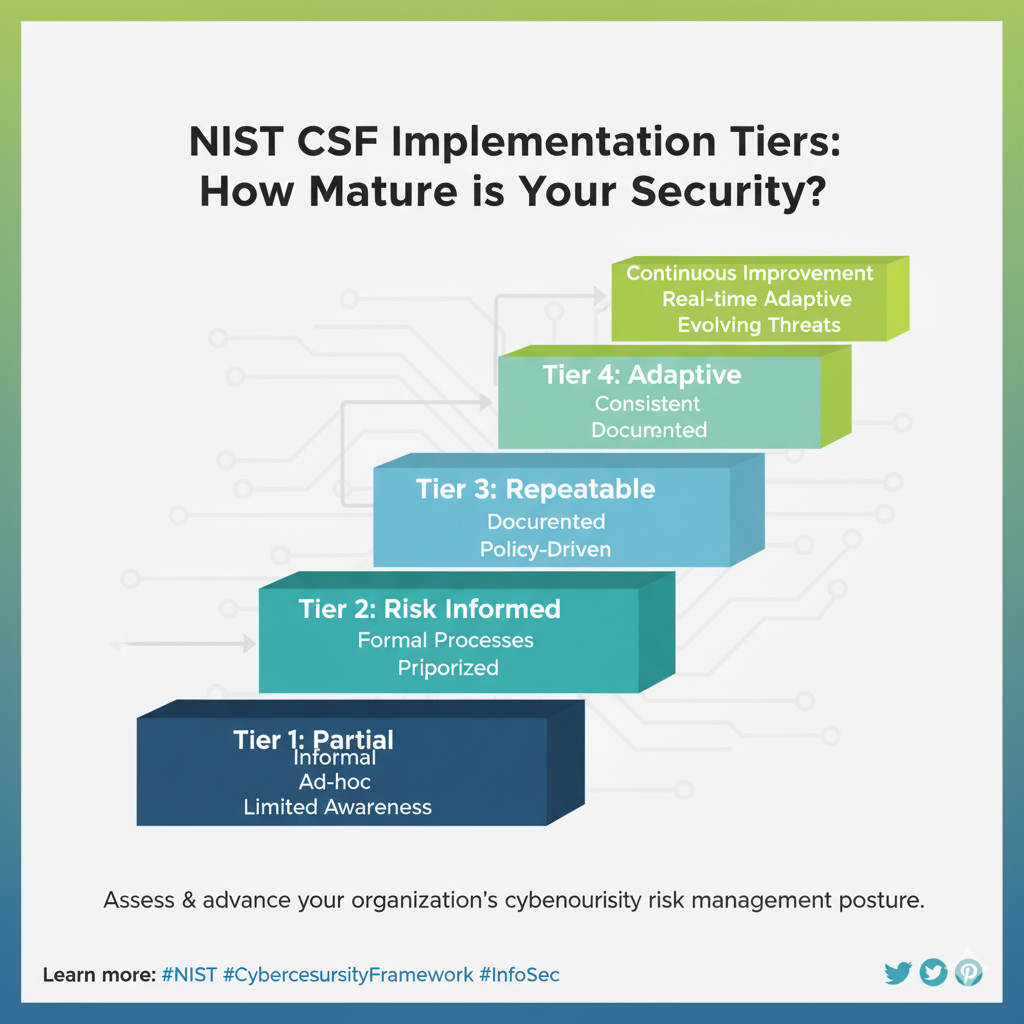
Implementation Tiers: Understanding Your Cybersecurity Maturity
The NIST CSF also includes Implementation Tiers, which describe the degree to which an organization’s cybersecurity risk management practices exhibit the characteristics defined in the Framework.
These tiers provide context on how an organization views cybersecurity risks and the processes in place to manage those risks.
It’s important to note that tiers do not necessarily represent maturity levels in a rigid sense; rather, they help organizations understand the rigor and integration of their cybersecurity risk decisions.
The Tiers range from Partial (Tier 1) to Adaptive (Tier 4), indicating an increasing degree of rigor and how well integrated cybersecurity risk decisions are into broader risk decisions.
They also reflect the extent to which an organization shares and receives cybersecurity information from external parties.
Tier 1: Partial: Cybersecurity risk management is informal, and an organization may not have prioritized cybersecurity activities.
There is little to no awareness of cybersecurity risk at the organizational level.
Tier 2: Risk Informed: Cybersecurity risk management practices are approved by management but may not be fully integrated throughout the organization. There’s an awareness of cybersecurity risk, but it might not be consistently applied across all departments.
Tier 3: Repeatable: Cybersecurity risk management practices are formally approved, documented, and consistently implemented.
The organization has a repeatable process for managing cybersecurity risks, and information sharing with external partners is becoming more common.
Tier 4: Adaptive: Cybersecurity risk management practices are continuously adapted based on previous cybersecurity activities and evolving threats.
The organization actively shares and receives cybersecurity information, and cybersecurity risk management is fully integrated into the organization’s overall risk management strategy.
This tier represents a highly proactive and mature approach.
Organizations should determine their desired Tier based on their specific goals, risk appetite, and the feasibility of implementation.
The aim is to reduce cybersecurity risk to levels acceptable to the organization, not necessarily to reach Tier 4 if it’s not appropriate for their context.
Framework Profiles: Tailoring the CSF to Your Organization
Framework Profiles are a critical component of the NIST CSF, allowing organizations to customize the framework to their unique needs.
A Profile represents an organization’s specific alignment of its requirements, objectives, and risk appetite against the desired outcomes of the Framework Core.
It’s about making the CSF work for your organization, rather than forcing your organization to fit the CSF.
Profiles can be incredibly useful for identifying opportunities to improve cybersecurity posture.
This is often done by comparing a “Current” Profile with a “Target” Profile.
The Current Profile reflects the organization’s cybersecurity activities and outcomes as they exist today, while the Target Profile outlines the desired state based on risk assessments, business objectives, and regulatory requirements.
The process of creating Profiles typically involves:
1. Identifying Business Requirements: Understanding the organization’s mission, business objectives, and critical services.
2. Mapping to the Framework Core: Aligning current cybersecurity practices and desired outcomes with the Functions, Categories, and Subcategories of the CSF Core.
3. Conducting a Gap Analysis: Comparing the Current Profile with the Target Profile to identify discrepancies and areas where improvements are needed.
4. Developing an Action Plan: Creating a prioritized plan to address the identified gaps, considering factors like risk priority, cost, and feasibility.
Since the Framework is voluntary, there’s no single
‘right’ or ‘wrong’ way to implement it. Profiles empower organizations to optimize the CSF to best serve their specific context, making it a highly adaptable tool for cybersecurity risk management.
Conclusion
The NIST Cybersecurity Framework, with its Core (Functions, Categories, and Subcategories), Implementation Tiers, and Profiles, offers a robust and flexible approach for organizations to manage their cybersecurity risks.
It provides a common language, a structured methodology, and a pathway for continuous improvement, helping organizations of all types and sizes to build more resilient and secure environments.
By understanding and effectively utilizing these components, businesses can proactively address cyber threats, protect their valuable assets, and ensure operational continuity in an increasingly digital world.
References
* NIST. (2024, February 26). *The NIST Cybersecurity Framework (CSF) 2.0*. Retrieved from []
(https://nvlpubs.nist.gov/nistpubs/CSWP/NIST.CSWP.29.pdf)
* NIST. (2018, February 6). *Cybersecurity Framework 1.1 Components*. Retrieved from []
(https://www.nist.gov/cyberframework/cybersecurity-framework-components)
