
The landscape of web application security is a dynamic and often perilous environment.
For over two decades, one document has served as the definitive guide for developers, security professionals, and organizations worldwide: the OWASP Top 10.
This list, compiled and maintained by the non-profit Open Web Application Security Project (OWASP), represents a broad consensus of the most critical security risks facing web applications today [1].
Understanding and mitigating these ten risks is not merely a best practice; it is a fundamental requirement for building secure, resilient software.
This comprehensive guide will delve into the 2021 edition of the OWASP Top 10, breaking down each vulnerability, illustrating its potential impact with real-world scenarios, and outlining the precise, actionable steps required for prevention.
By mastering these concepts, you can effectively “shift left” in your development lifecycle, embedding security from the design phase rather than attempting to patch vulnerabilities later.
What is the OWASP Top 10 and Why Does it Matter?
The OWASP Top 10 is more than just a list of flaws; it is a powerful awareness document that drives changes in software development culture.
It is globally recognized as the first step toward more secure coding and is used by companies to ensure their web applications minimize critical risks [1].
The 2021 version introduced three new categories, renamed several others, and reordered the list based on extensive data from the security community, demonstrating an evolving focus on design and integrity risks.
The significance of this list lies in its ability to prioritize security efforts.
By focusing on the Top 10, organizations can address the most common and impactful vulnerabilities that attackers actively exploit.
The vulnerabilities are ranked based on a combination of factors, including exploitability, detectability, and, most importantly, the technical and business impact of a successful attack.
https://www.youtube.com/live/tOODAwc–Uc?si=DOiE3WU5w9If5XVb
A01:2021 – Broken Access Control
Broken Access Control is the number one risk in the 2021 list, moving up from fifth place in the previous edition.
This vulnerability occurs when an application fails to properly enforce restrictions on what authenticated users are allowed to do.
Access control enforces policy such that users cannot act outside of their intended permissions, and failures typically lead to unauthorized information disclosure, modification, or destruction of data [2].
Description and Scenarios
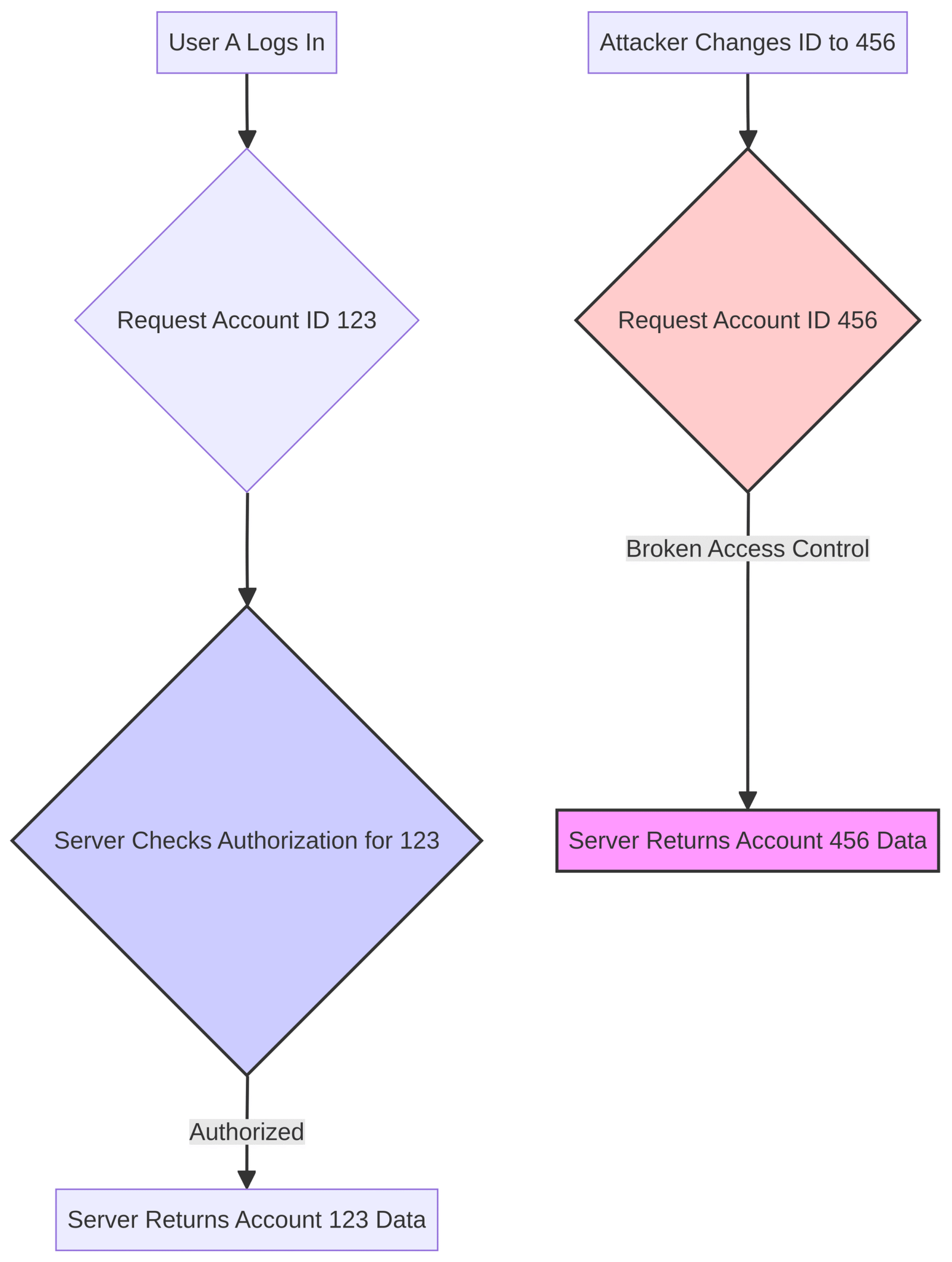
A common scenario involves a user modifying a URL parameter to access another user’s account data, a flaw known as an Insecure Direct Object Reference (IDOR).
For example, if a URL to view an account is https://example.com/app/accountInfo?acct=12345, an attacker might simply change the acct parameter to 54321 to view a different user’s information.
Other failures include elevation of privilege, where a standard user gains administrative rights, or force browsing to authenticated pages as an unauthenticated user.
The core issue is a violation of the principle of least privilege, where access is granted by default instead of being explicitly restricted [2].
Prevention Measures
Access control must be enforced in trusted server-side code or server-less APIs, where the attacker cannot modify the checks.
The golden rule is to deny by default for all public resources.
Developers should implement access control mechanisms once and reuse them throughout the application, ensuring they enforce record ownership.
It is also crucial to log all access control failures and alert administrators when repeated failures suggest an automated attack [2].
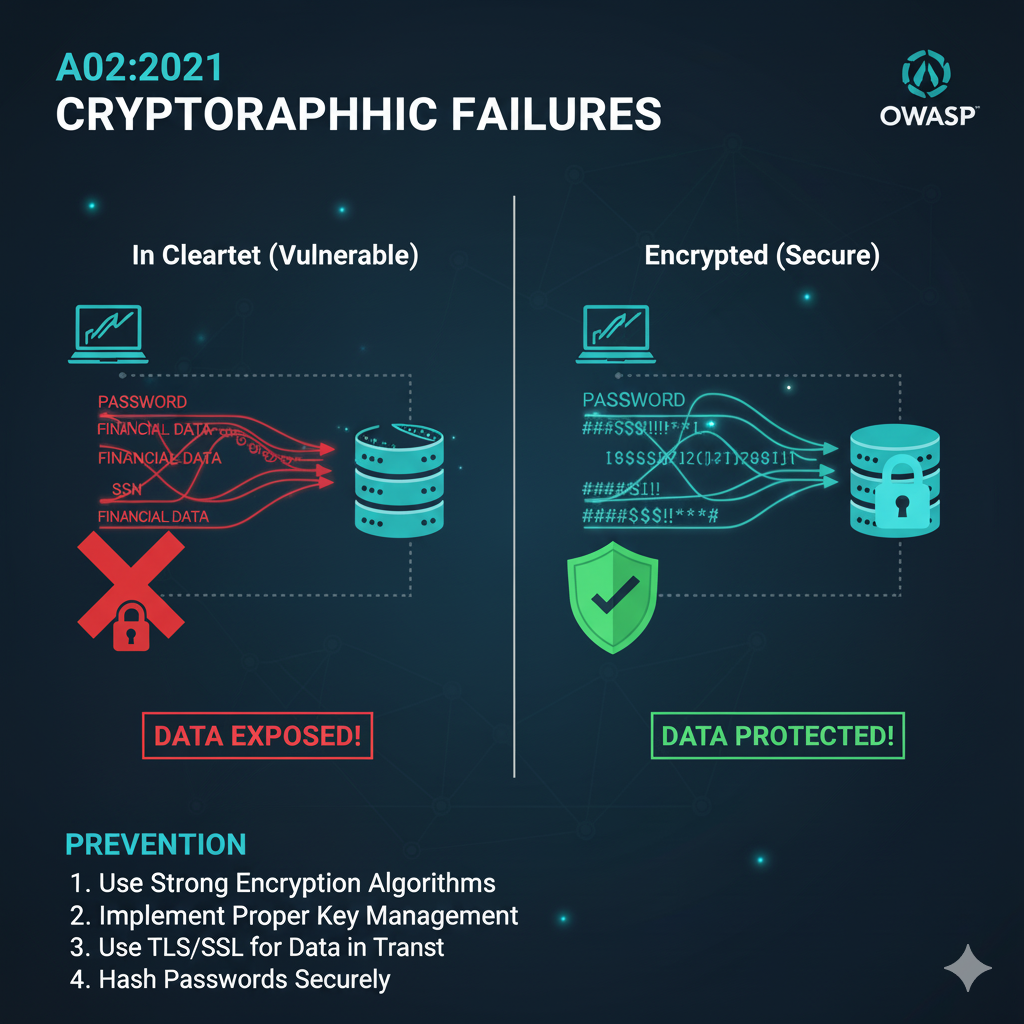
A02:2021 – Cryptographic Failures
Formerly known as “Sensitive Data Exposure,” this category focuses on the root cause: failures related to cryptography or the complete lack thereof.
These failures often lead to the exposure of sensitive data such as passwords, credit card numbers, and personal information.
The vulnerability moves up one position to number two, highlighting the critical nature of data protection [3].
Description and Scenarios
Cryptographic failures occur when sensitive data is transmitted in clear text, old or weak cryptographic algorithms are used, or proper key management is missing.
A classic scenario is an application that encrypts credit card numbers in a database but automatically decrypts them upon retrieval, allowing a separate vulnerability, like SQL Injection, to retrieve the data in clear text.
Another common failure is the use of unsalted or simple hashes for storing passwords, making them vulnerable to rainbow table attacks [3].
Prevention Measures
The first step is to classify all data and identify what is sensitive according to privacy laws (e.g., GDPR) or business needs.
Developers must ensure all sensitive data is encrypted at rest and in transit using up-to-date, strong standard algorithms and protocols like TLS with forward secrecy (FS) ciphers.
For passwords, the use of strong, adaptive, and salted hashing functions like Argon2, scrypt, or bcrypt is mandatory [3].
A03:2021 – Injection
Injection, which includes SQL, NoSQL, OS command, and Cross-Site Scripting (XSS), remains a perennial threat, though it slides down to the third position.
An application is vulnerable to injection when user-supplied data is not properly validated, filtered, or sanitized before being passed to an interpreter as part of a command or query [4].
Description and Scenarios
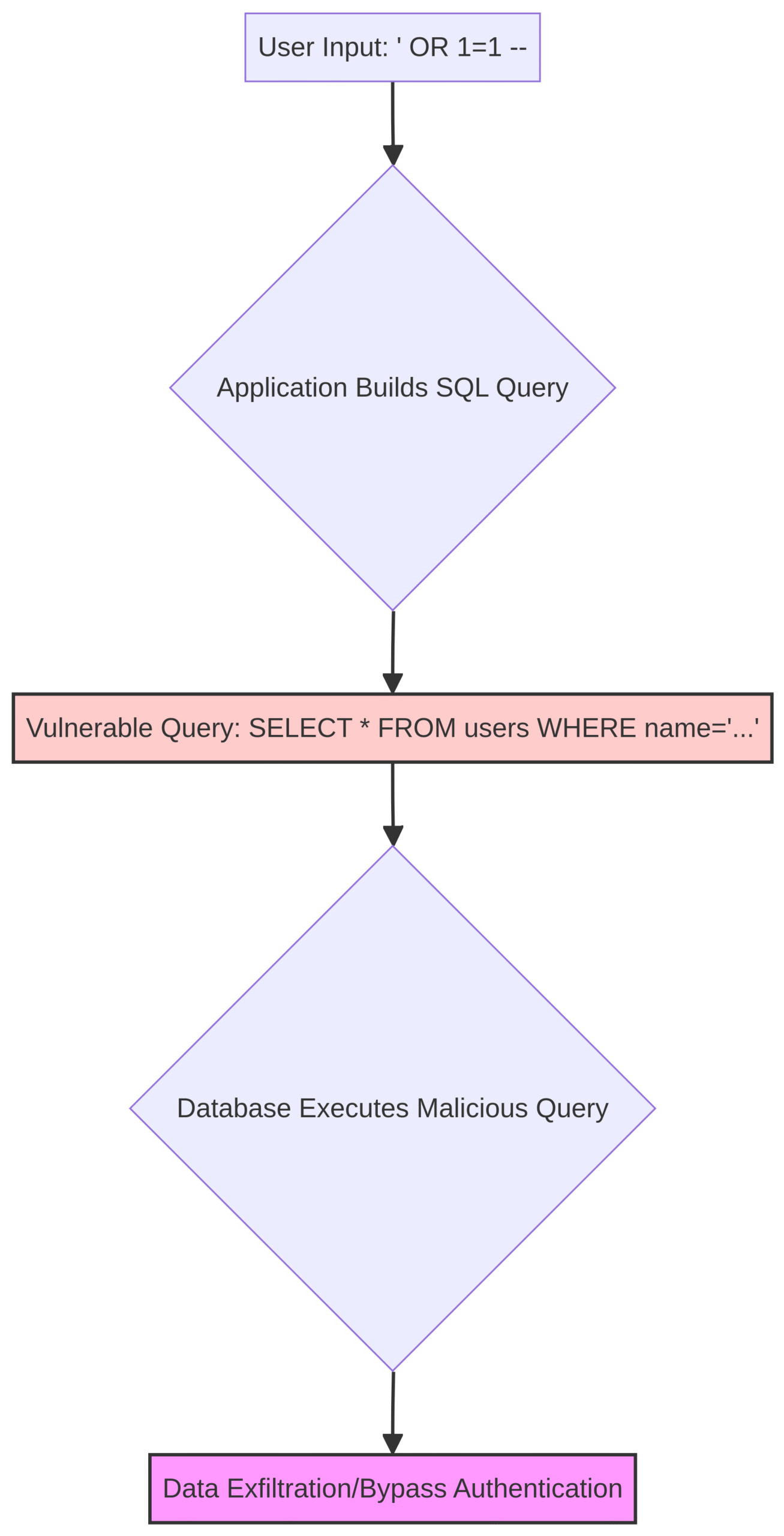
The most infamous example is SQL Injection (SQLi), where an attacker modifies a query to execute arbitrary SQL commands.
If an application uses a vulnerable query like SELECT * FROM accounts WHERE custID='[user_input]', an attacker can input ' OR 1=1 -- to bypass authentication or ' UNION SELECT SLEEP(10);-- to test for vulnerability.
The core problem is the mixing of untrusted data with command or query structure [4].
Prevention Measures
The preferred method for preventing injection is to keep data separate from commands and queries.
This is best achieved by using safe APIs that avoid the interpreter entirely, such as parameterized queries (prepared statements) or Object Relational Mapping (ORM) tools.
Positive server-side input validation, which only allows known-good input, should also be used as a defense-in-depth measure [4].
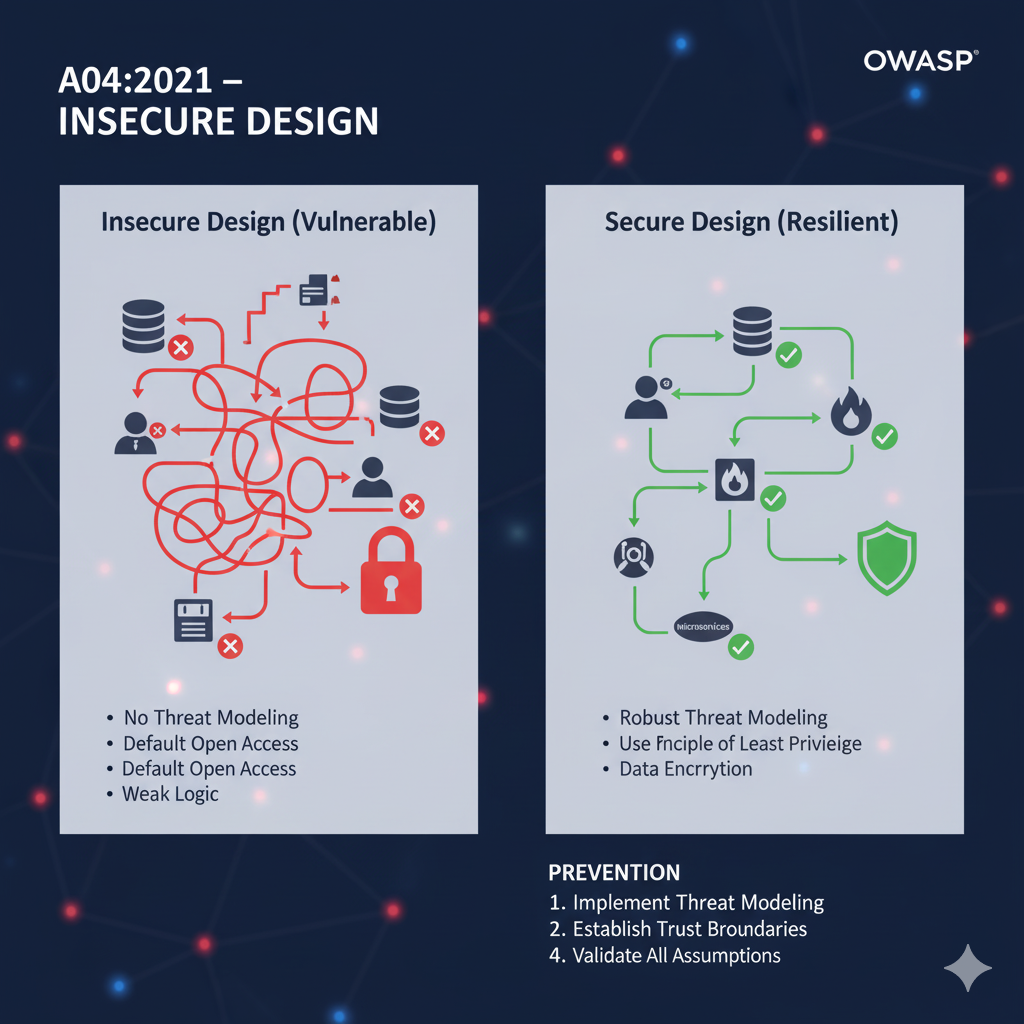
A04:2021 – Insecure Design
This is a new category for 2021, focusing on risks related to design and architectural flaws rather than implementation defects.
It emphasizes the need for a “Secure by Design” approach, which involves pre-code activities like threat modeling and using secure design patterns [5].
An insecure design cannot be fixed by a perfect implementation because the necessary security controls were never created in the first place.
Description and Scenarios
Insecure design is a broad category, often expressed as “missing or ineffective control design.”
Examples include a credential recovery workflow that uses “questions and answers,” which is inherently insecure and prohibited by modern standards like NIST 800-63b.
Another scenario is a lack of anti-bot design on an e-commerce site, allowing “scalpers” to automate purchases and deplete inventory, causing business loss and reputational damage [5].
Prevention Measures
Prevention requires establishing a Secure Development Lifecycle (SDL).
Key measures include using threat modeling for critical components (authentication, access control, business logic), integrating security language into user stories, and writing unit and integration tests to validate resistance to the threat model.
It is also vital to segregate tier layers on the system and network levels based on exposure and protection needs [5].
A05:2021 – Security Misconfiguration
Moving up from the sixth position, Security Misconfiguration is a common and often easily preventable risk.
It occurs when security settings are either missing or improperly configured across the application stack, including the operating system, web server, application server, database, and frameworks [6].
Description and Scenarios
Vulnerabilities in this category include using default accounts and passwords, enabling unnecessary features or services, and failing to remove sample applications from a production server.
A critical misconfiguration is the failure to disable directory listing, which allows an attacker to browse directories and potentially download sensitive files like compiled Java classes for reverse engineering.
Another common issue is overly informative error messages, such as stack traces, which can expose sensitive information about the application’s underlying architecture and component versions [6].
Prevention Measures
Prevention hinges on a repeatable, automated hardening process.
This process should ensure a minimal platform is deployed, with all unnecessary features and components removed.
Configurations must be reviewed and updated as part of a regular patch management process.
Furthermore, an automated process should verify the effectiveness of configurations in all environments (Development, QA, and Production) to ensure they are identical and securely locked down [6].
A06:2021 – Vulnerable and Outdated Components
This category, formerly “Using Components with Known Vulnerabilities,” is a persistent problem in modern software development, which relies heavily on third-party libraries and frameworks.
It highlights the risk posed by using components that are vulnerable, unsupported, or out of date [7].
Since components run with the same privileges as the application itself, a flaw in a single component can have a catastrophic impact.
Description and Scenarios
A system is vulnerable if developers do not know the versions of all components, including nested dependencies, or if they fail to regularly scan for vulnerabilities.
A notorious example is the 2017 Equifax breach, which was attributed to a known vulnerability in the Apache Struts framework [7].
Another scenario involves using components that are unmaintained or no longer receive security patches, leaving the application permanently exposed to fixed vulnerabilities.
Prevention Measures
Organizations must implement a robust patch management process.
This includes continuously inventorying all client-side and server-side components and their dependencies using Software Composition Analysis (SCA) tools like OWASP Dependency Check.
Components should only be obtained from official sources over secure links, and unused dependencies must be removed.
Monitoring sources like the Common Vulnerability and Exposures (CVE) and National Vulnerability Database (NVD) is essential for timely patching [7].
A07:2021 – Identification and Authentication Failures
This category, previously “Broken Authentication,” now includes identification failures and focuses on weaknesses in confirming a user’s identity and managing their session.
Failures in this area can allow attackers to compromise user accounts, assume identities, and gain unauthorized access [8].
Description and Scenarios
Vulnerabilities include permitting automated attacks like credential stuffing, where attackers use lists of stolen credentials from other breaches to gain access.
Other failures involve using weak or ineffective credential recovery processes, such as “knowledge-based answers,” which are easily compromised.
Session management flaws, such as exposing session identifiers in the URL or failing to properly invalidate session IDs after logout or inactivity, also fall into this category [8].
Prevention Measures
The most effective defense is the implementation of Multi-Factor Authentication (MFA) to prevent automated attacks and credential reuse.
Organizations should align password policies with modern standards like NIST 800-63b, which discourages mandatory password rotation and complexity requirements in favor of strong, long passphrases.

A secure, server-side session manager that generates a new, high-entropy session ID after login and invalidates it upon logout is also critical [8].
A08:2021 – Software and Data Integrity Failures
This new category for 2021 highlights the risks associated with making assumptions about the integrity of software updates, critical data, and CI/CD pipelines.
It focuses on the failure to verify that code and data have not been tampered with [9].
This vulnerability has one of the highest weighted impacts, reflecting the severity of supply chain attacks.
Description and Scenarios
Integrity failures occur when an application relies on plugins, libraries, or modules from untrusted sources without verifying their authenticity.
A prime example is the SolarWinds Orion attack, where attackers subverted the company’s build process to distribute a highly targeted malicious update to thousands of organizations [9].
Another scenario is Insecure Deserialization, where an attacker can modify encoded or serialized data to execute remote code on the application server.
Prevention Measures
Prevention requires the use of digital signatures or similar mechanisms to verify that software and data originate from the expected source and have not been altered.
CI/CD pipelines must have proper segregation and access control to ensure the integrity of the code flow.
For dependencies, organizations should consume trusted repositories and consider hosting an internal, vetted repository for higher-risk profiles [9].
A09:2021 – Security Logging and Monitoring Failures
Moving up from the tenth position in the 2017 list, this category is crucial for the detection, escalation, and response to active breaches.
Without sufficient logging and monitoring, a breach can go undetected for months or even years, leading to catastrophic data loss [10].
Description and Scenarios
Failures include not logging auditable events (logins, failed logins, high-value transactions), generating inadequate or unclear log messages, and failing to monitor logs for suspicious activity.
A real-world scenario involves a health plan provider that could not detect a breach due to a lack of monitoring, which was only discovered when an external party informed them that an attacker had accessed millions of sensitive health records [10].
The absence of real-time alerting means that attacks can proceed unimpeded.
Prevention Measures
Developers must ensure all access control and server-side input validation failures are logged with sufficient user context.
Logs should be generated in a format easily consumed by log management solutions (e.g., ELK stack) and should be protected with integrity controls to prevent tampering.
Establishing effective monitoring and alerting is paramount, as is having a formal incident response and recovery plan [10].
A10:2021 – Server-Side Request Forgery (SSRF)
The final new category for 2021, Server-Side Request Forgery (SSRF), was added based on community feedback and data showing its high exploit and impact potential.
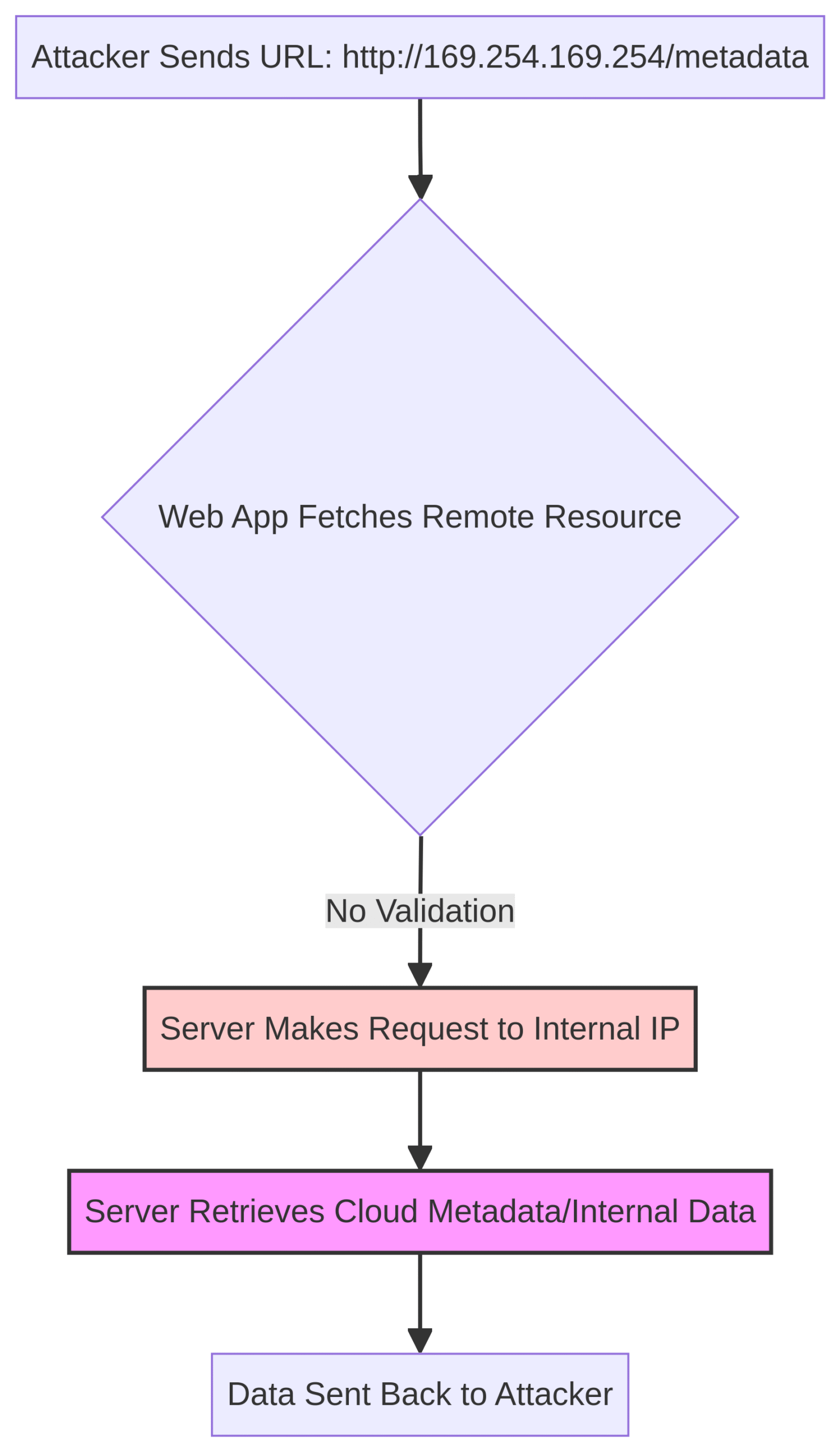
SSRF occurs when a web application fetches a remote resource without validating the user-supplied URL, allowing an attacker to coerce the application to send a crafted request to an unexpected destination [11].
Description and Scenarios
SSRF is particularly dangerous because it allows attackers to bypass firewalls and access internal systems.
A common attack is to use SSRF to port scan internal servers or access sensitive local files, such as file:///etc/passwd.
In cloud environments, attackers can exploit SSRF to access the cloud provider’s metadata storage (e.g., http://169.254.169.254/), which often contains highly sensitive information like temporary credentials [11].
Prevention Measures
Prevention requires a defense-in-depth approach, starting with network-level segmentation to reduce the impact of SSRF.
At the application layer, developers must sanitize and validate all client-supplied input data and enforce the URL schema, port, and destination with a positive allow list.

Crucially, developers should never attempt to mitigate SSRF using a deny list or regular expressions, as these are easily bypassed by skilled attackers [11].
Summary of the OWASP Top 10 (2021)
The 2021 edition of the OWASP Top 10 represents a significant evolution in application security awareness.
The table below summarizes the key changes and the core focus of each vulnerability [1, 12].
| Rank (2021) | Vulnerability Name | Previous Rank (2017) | Core Focus |
|---|---|---|---|
| A01 | Broken Access Control | A05 | Unauthorized access to data or functionality due to flawed enforcement of user permissions. |
| A02 | Cryptographic Failures | A03 (Sensitive Data Exposure) | Failures in data protection, including weak encryption, poor key management, and cleartext storage. |
| A03 | Injection | A07 | Mixing untrusted data with command or query structure (e.g., SQLi, XSS). |
| A04 | Insecure Design | New Category | Flaws in the application’s architecture or design, requiring a “Secure by Design” approach. |
| A05 | Security Misconfiguration | A06 | Insecure default configurations, incomplete hardening, or overly permissive settings. |
| A06 | Vulnerable and Outdated Components | A09 | Using libraries, frameworks, or other components with known security flaws. |
| A07 | Identification and Authentication Failures | A02 (Broken Authentication) | Weaknesses in user identity confirmation, session management, and credential recovery. |
| A08 | Software and Data Integrity Failures | New Category | Making assumptions about the integrity of software updates, critical data, and CI/CD pipelines. |
| A09 | Security Logging and Monitoring Failures | A10 (Insufficient Logging & Monitoring) | Lack of logging, detection, and real-time alerting necessary to detect and respond to breaches. |
| A10 | Server-Side Request Forgery (SSRF) | New Category | Attacker forcing the server to make unauthorized requests to internal or external resources. |
The Path Forward: Embracing a Proactive Security Posture
The OWASP Top 10 is a living document, constantly evolving to reflect the changing threat landscape.
The inclusion of Insecure Design and Software and Data Integrity Failures signals a crucial shift in focus from fixing implementation bugs to addressing fundamental architectural and supply chain risks.
For any organization committed to digital security, the goal must be to move beyond simple compliance and embrace a truly proactive security posture.
This involves integrating security practices throughout the entire Software Development Lifecycle (SDLC), from initial design and threat modeling to continuous monitoring and incident response.
By treating the OWASP Top 10 not as a checklist for compliance but as a roadmap for security excellence, developers and security teams can build applications that are inherently more secure and resilient against the most critical threats.
The effort required to secure an application is always less than the cost of a data breach.
Start today by auditing your applications against these ten risks and making a commitment to secure coding practices.
References
[1] OWASP Top Ten | OWASP Foundation
[2] A01 Broken Access Control – OWASP Top 10:2021
[3] A02 Cryptographic Failures – OWASP Top 10:2021
[4] A03 Injection – OWASP Top 10:2021
[5] A04 Insecure Design – OWASP Top 10:2021
[6] A05 Security Misconfiguration – OWASP Top 10:2021
[7] A06 Vulnerable and Outdated Components – OWASP Top 10:2021
[8] A07 Identification and Authentication Failures – OWASP Top 10:2021
[9] A08 Software and Data Integrity Failures – OWASP Top 10:2021
[10] A09 Security Logging and Monitoring Failures – OWASP Top 10:2021
[11] A10 Server Side Request Forgery (SSRF) – OWASP Top 10:2021
[12] Introduction – OWASP Top 10:2021
Books recommended




