Here you will find posts about Cyber security and it’s best practices – also, you can search your queries for different results
-
VPN vs. Zero Trust Network Access: Navigating Modern Security Frameworks
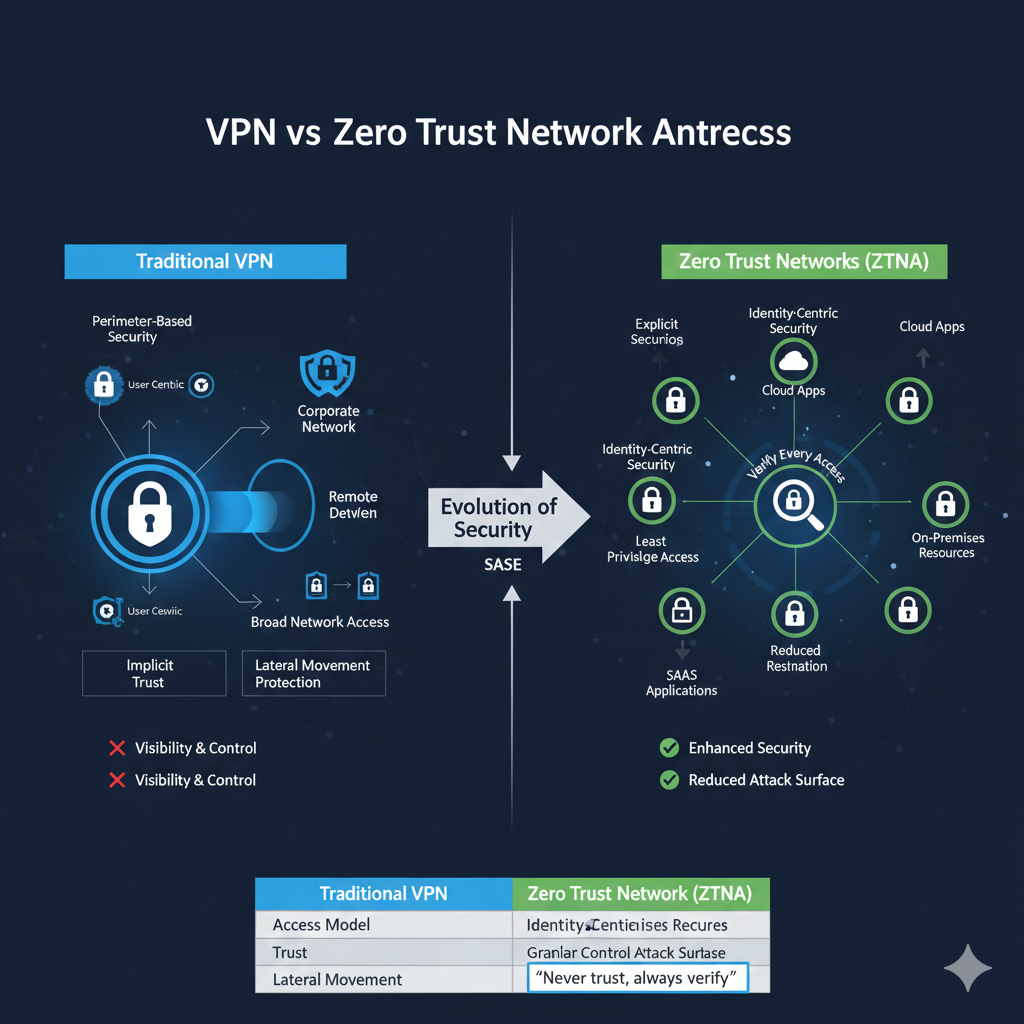
Explore the differences between VPNs and Zero Trust Network Access (ZTNA) to understand modern security frameworks and choose the best approach for your organization.
-
Application Security: ISO 27001 vs. NIST Cybersecurity Framework – A Comprehensive Comparison
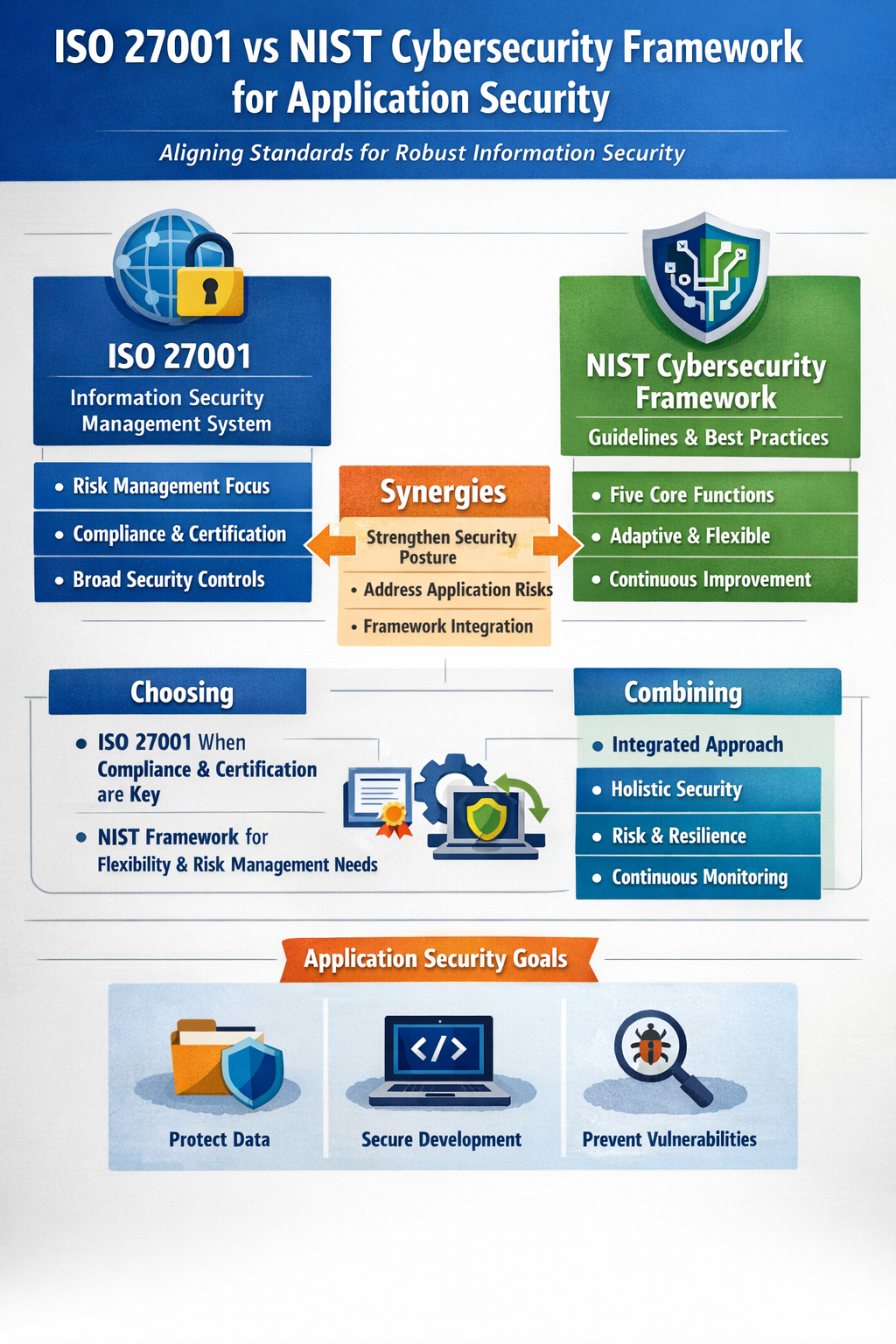
Delve into ISO 27001 and the NIST Cybersecurity Framework for application security. Understand their differences, synergies, and how to choose or combine them for robust information security management. Application Security
-
Automated Testing and Troubleshooting with CI/CD Pipelines

Master the art of automated testing and troubleshooting within CI/CD pipelines. Learn to implement the testing pyramid, diagnose common pipeline failures, and build a resilient, self-healing delivery process. Automated Testing and Troubleshooting with CI/CD Pipelines
-
VPN Tunneling Protocols Compared: Choosing the Right Security for Your Network
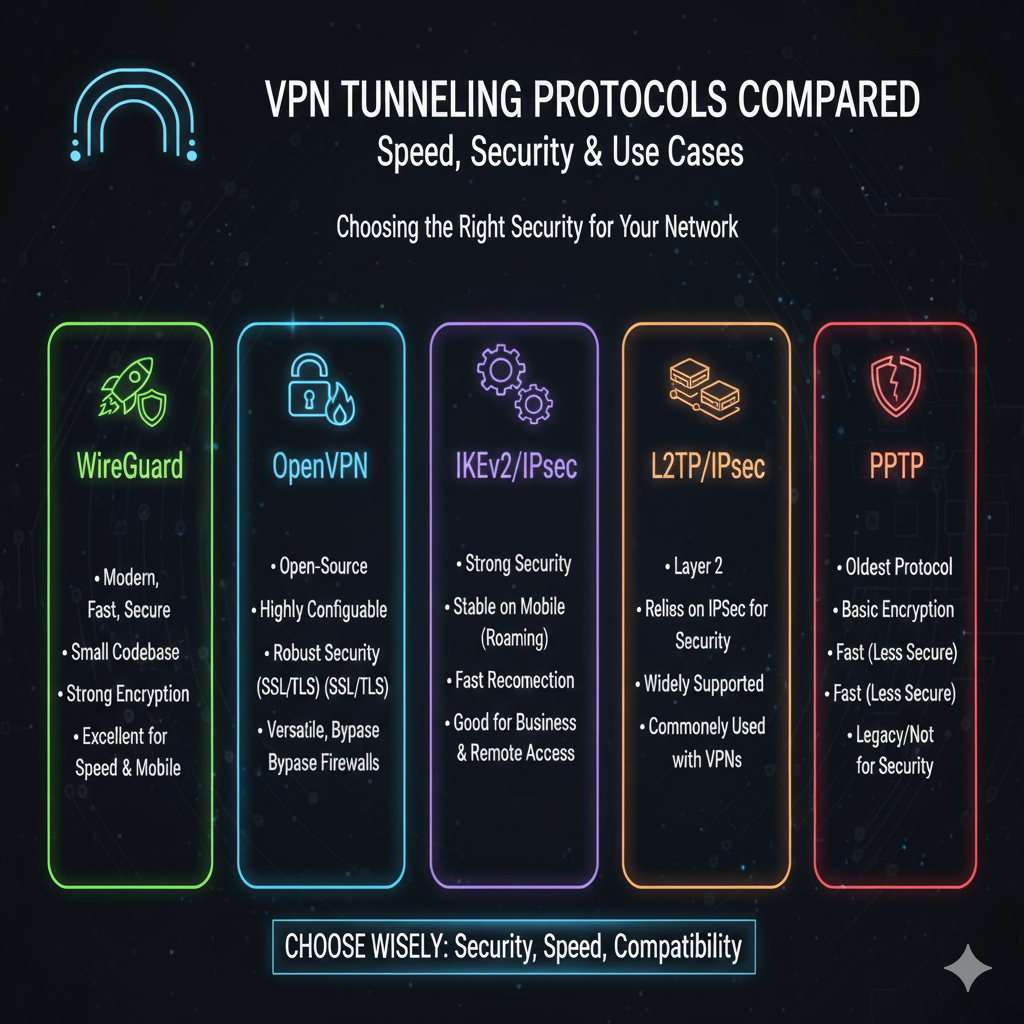
A deep dive comparison of the most popular VPN tunneling protocols, including WireGuard, OpenVPN, IKEv2/IPsec, L2TP/IPsec, and PPTP, to help you choose the best one for speed and security.
-
Email Protocols Explained: SMTP, POP3, and IMAP Differences Demystified

A clear comparison of the three essential email protocols—SMTP, POP3, and IMAP—explaining their roles in sending and receiving email, their key differences, and which one is best for your needs. Email protocols
-
Edge Computing Network Architecture: Bringing Processing Power Closer to the Data Source
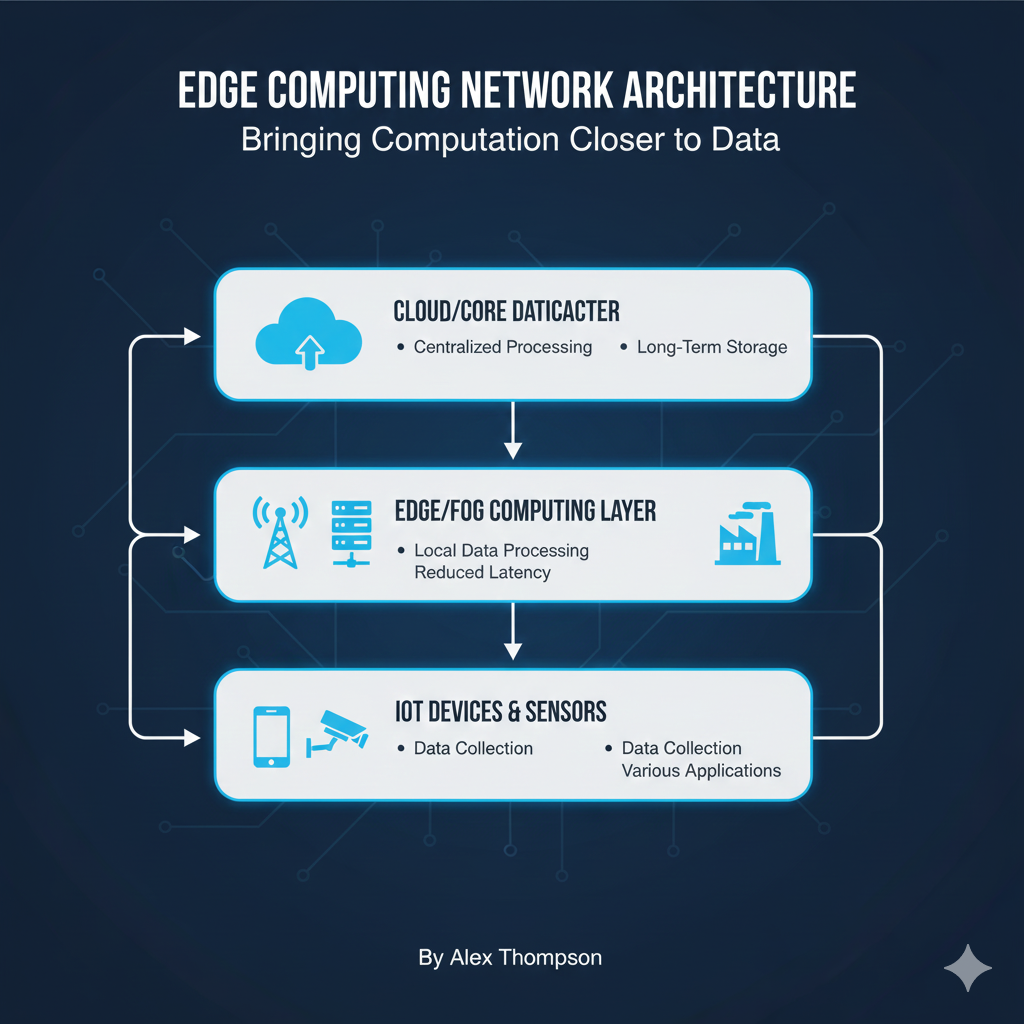
Explore the distributed network architecture of Edge Computing, its core components (devices, gateways, servers), and how it reduces latency and enhances real-time processing for IoT and 5G applications.
-
Multi-Factor Authentication Types Comparison: Choosing the Right Layer of Security

A detailed comparison of the different types of Multi-Factor Authentication (MFA), including knowledge, possession, and inherence factors, and a guide to selecting the most secure and user-friendly method for your organization. Multi-Factor Authentication
-
Symmetric vs. Asymmetric Encryption Explained: The Foundation of Modern Cybersecurity

A detailed comparison of symmetric (single-key) and asymmetric (public/private key pair) encryption, explaining how they work, their pros and cons, and their combined role in securing the internet (TLS/SSL). Symmetric vs. Asymmetric Encryption
-
Cybersecurity Principles for Beginners: Mastering the Fundamentals of Digital Defense

A beginner’s guide to the core principles of cybersecurity, focusing on the CIA Triad (Confidentiality, Integrity, Availability) and essential best practices for protecting personal and professional digital assets.Cybersecurity Principles for Beginners:
