In today’s interconnected world, cyber threats are not a matter of if, but when.
Every organization, regardless of size or industry, faces the constant risk of security incidents that can disrupt operations, compromise data, and damage reputation.
This is where an IT Incident Response Plan (IRP) becomes your indispensable blueprint for cyber resilience.
An IRP is a structured approach that an organization follows to prepare for, detect, contain, and recover from cybersecurity incidents.
It’s more than just a document; it’s a strategic framework designed to minimize the impact of an attack and ensure business continuity.
Without a well-defined IRP, a security incident can quickly spiral into a crisis, leading to significant financial losses and long-term consequences.
Having a robust plan in place allows your team to act swiftly and effectively, transforming potential chaos into a controlled and manageable situation
Videos will be added as random thoughts 💭 💭 💭
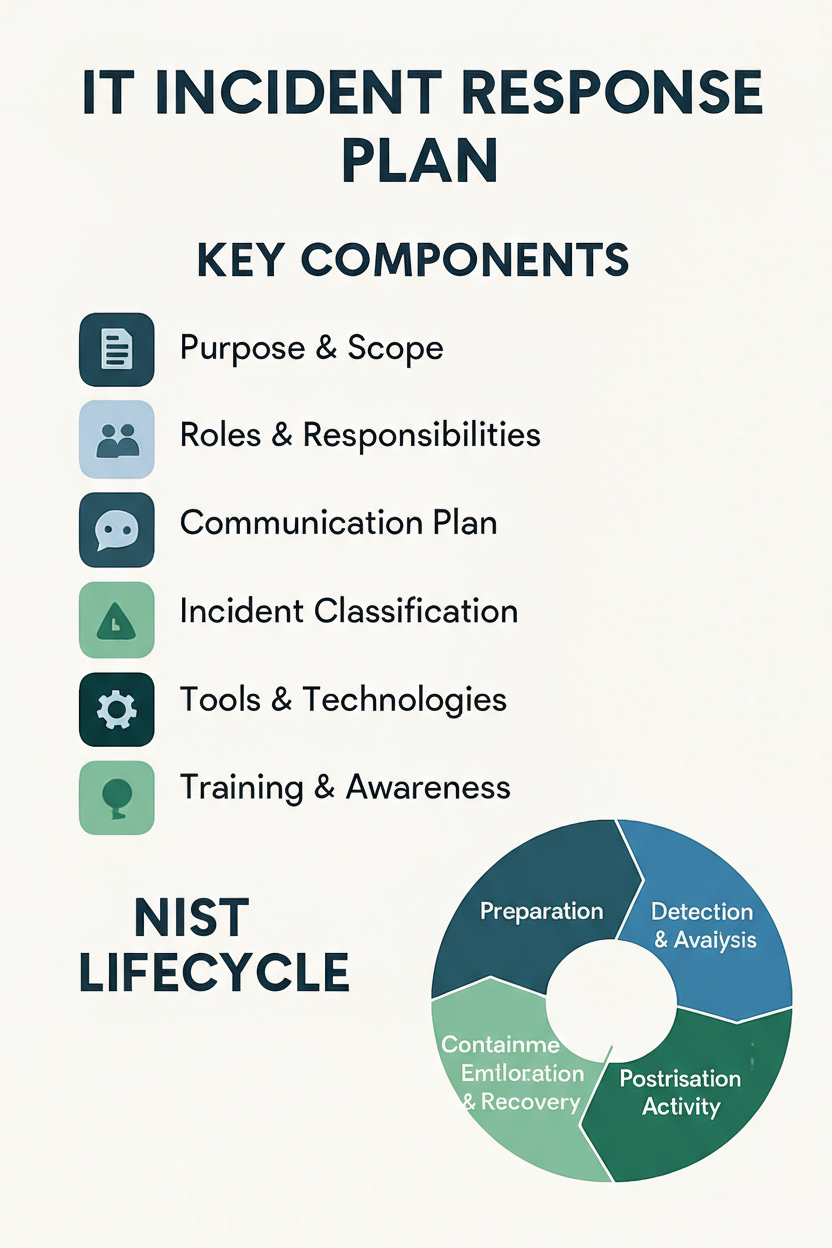
The Core Components of an Effective IRP
A truly effective IT Incident Response Plan isn’t just a single document; it’s a living framework built upon several critical components.
These elements work in concert to provide clarity, direction, and efficiency when an incident strikes.
Let’s dive into what makes up a robust IRP.
First, every IRP needs a clear Purpose and Scope.
This section defines why the plan exists, what types of incidents it covers (e.g., malware, data breaches, denial-of-service attacks), and which systems, data, and personnel fall under its purview.
It sets the boundaries and expectations for the entire response effort, ensuring everyone understands the plan’s objectives and limitations.
Next, identifying Roles and Responsibilities is paramount.
An incident response is a team effort, and ambiguity can lead to delays and missteps.
Your IRP should clearly outline who is on the incident response team, their contact information, their specific duties, and their reporting structure.
This includes defining roles like incident commander, technical lead, communications lead, legal counsel, and human resources representatives.
Knowing who does what, and when, is crucial for a coordinated response [1].
A robust Communication Plan is another cornerstone.
During an incident, timely and accurate communication is vital, both internally and externally.
This component details how information will be shared with stakeholders, including employees, management, customers, partners, and regulatory bodies.
It should specify communication channels, approved messaging, and escalation procedures.
Transparency and clear communication can help maintain trust and mitigate reputational damage.
Incident Classification and Prioritization provides a standardized way to assess the severity and impact of an incident.
Not all incidents are created equal, and your plan should include criteria for categorizing incidents (e.g., low, medium, high criticality) and a process for prioritizing response efforts based on potential business impact.
This ensures that critical incidents receive immediate attention and resources.
Considering the Tools and Technologies at your disposal is also essential.
Your IRP should list the security tools, software, and hardware that will be used during an incident response.
This might include security information and event management (SIEM) systems, intrusion detection/prevention systems (IDS/IPS), forensic tools, and secure communication platforms.
Knowing your toolkit beforehand streamlines the response process.
Finally, Training and Awareness cannot be overlooked.
An IRP is only as good as the people who execute it.
Regular training for the incident response team ensures they are proficient in their roles and familiar with the plan’s procedures.
Furthermore, general security awareness training for all employees can help prevent many incidents from occurring in the first place, making them the first line of defense.
The Incident Response Lifecycle (NIST Framework)
To provide a structured and comprehensive approach to incident response, many organizations adopt frameworks like the one developed by the National Institute of Standards and Technology (NIST).
The NIST Incident Response Lifecycle is widely recognized and consists of four key phases:
Preparation, Detection and Analysis, Containment, Eradication, and Recovery, and Post-Incident Activity [2].
This cyclical model emphasizes continuous improvement and learning from each incident.
Preparation
The Preparation phase is foundational.
It involves all the activities undertaken before an incident occurs to ensure the organization is ready to respond effectively.
This includes establishing policies and procedures, forming and training the incident response team, acquiring necessary tools and technologies, and conducting risk assessments.
A critical aspect of preparation is identifying critical assets, understanding their vulnerabilities, and implementing preventative measures.
This phase also involves developing communication plans and ensuring that all team members know their roles and responsibilities.
Regular review and updates of the plan, at least annually or more frequently with significant changes in the threat landscape, are crucial to maintain its effectiveness [3].
Detection and Analysis
The Detection and Analysis phase focuses on identifying and assessing potential security incidents.
This involves continuous monitoring of systems and networks for anomalies, security alerts, and suspicious activities.
Once a potential incident is detected, the team must analyze it to determine its nature, scope, and severity.
This includes gathering evidence, correlating events, and prioritizing the incident based on its potential impact.
The goal is to quickly and accurately confirm an incident, understand what happened, and determine the appropriate response actions.
Effective detection relies on robust logging, monitoring tools, and skilled analysts who can interpret the data.
Containment, Eradication, and Recovery
Once an incident is confirmed and analyzed, the Containment, Eradication, and Recovery phase begins.
This is where the incident response team takes action to limit the damage and restore normal operations.
Containment involves isolating affected systems or networks to prevent the incident from spreading further.
This might include disconnecting devices, blocking malicious IP addresses, or shutting down compromised services.
After containment, Eradication focuses on removing the root cause of the incident, such as deleting malware, patching vulnerabilities, or reconfiguring systems.
Finally, Recovery involves restoring affected systems and data to their operational state, ensuring they are secure and fully functional.
This often includes restoring from backups, rebuilding systems, and rigorous testing to confirm the threat is gone and systems are stable.
Post-Incident Activity (Lessons Learned)
The final phase, Post-Incident Activity, is often overlooked but is vital for continuous improvement.
This phase involves conducting a thorough review of the incident, often referred to as a lessons learned review.
During this review, the team analyzes what happened, how well the response plan worked, what could have been done better, and what changes are needed to prevent similar incidents in the future.
This includes updating policies, procedures, and technologies, as well as refining training programs.
The insights gained from each incident are invaluable for strengthening the organization’s overall security posture and improving future incident response capabilities.
It’s a continuous feedback loop that ensures the IRP evolves with the threat landscape.
Best Practices for Building Your IRP
Developing an Incident Response Plan is a significant undertaking, but its effectiveness hinges on adhering to certain best practices.
These guidelines ensure your IRP is not just a document gathering dust, but a dynamic tool that genuinely protects your organization.
First and foremost, keep it flexible and adaptable.
The cyber threat landscape is constantly evolving, and no two incidents are exactly alike.
Your IRP should provide a solid framework but allow for flexibility to address unforeseen circumstances.
Avoid overly rigid procedures that might hinder quick decision-making in a crisis.
Regular review and updates are non-negotiable. An IRP is a living document that must evolve with your organization’s infrastructure, technologies, and the threat landscape.
NIST recommends reviewing and updating plans at least annually, or more frequently if there are significant changes [3].
This ensures the plan remains relevant and effective.
Perhaps the most critical best practice is to test your plan through drills and simulations.
A plan that hasn’t been tested is merely theoretical.
Conduct tabletop exercises, simulated attacks, and full-scale drills to identify weaknesses, refine procedures, and ensure your team can execute the plan under pressure.
These tests are invaluable for building muscle memory and confidence within the incident response team.
It’s also important to integrate with other policies.
Your IRP shouldn’t exist in a vacuum.
It needs to align with other organizational policies, such as disaster recovery plans, business continuity plans, and data privacy policies.
This ensures a cohesive and comprehensive approach to risk management.
Finally, focus on continuous improvement.
Every incident, whether real or simulated, is an opportunity to learn and improve.
Foster a culture of learning within your incident response team, encouraging open discussion about what went well and what could be improved.
This iterative process is key to building a truly resilient security program.
Key Considerations When Creating Your Template
When you sit down to create or customize an IT Incident Response Plan template, there are several critical considerations that will shape its effectiveness and relevance to your specific organization.
These are not just checkboxes but fundamental aspects that require careful thought and analysis.
One of the first steps is the identification of critical assets.
You cannot protect what you don’t know you have.
This involves cataloging all your essential hardware, software, data, and services.
Understanding which assets are most vital to your business operations allows you to prioritize protection and response efforts.
For example, a database containing customer information might be more critical than a public-facing marketing website.
Next, you must identify single points of failure in your network and address them.
A single point of failure is a part of a system that, if it fails, will stop the entire system from working.
These could be specific servers, network devices, or even key personnel.
Your IRP should include strategies to mitigate these risks, such as redundancy, load balancing, or cross-training of staff.
Finally, consider workforce continuity.
An incident can disrupt not only technology but also the ability of your employees to perform their jobs.
Your IRP should account for how your workforce will continue to operate during and after an incident.
This might involve remote work capabilities, alternative communication methods, or temporary relocation strategies.
Ensuring your people can continue to function is as important as restoring your systems.
Conclusion
In an era where cyber threats are a constant presence, an IT Incident Response Plan is no longer a luxury but a necessity.
It serves as your organization’s blueprint for navigating the turbulent waters of a security incident, transforming potential disaster into a manageable challenge.
By meticulously preparing, swiftly detecting, effectively containing, and diligently learning from every event, you build a foundation of cyber resilience that protects your assets, reputation, and continuity.
Don’t wait for an incident to happen.
Start building or refining your IT Incident Response Plan today.
Empower your team with the knowledge, tools, and processes they need to respond confidently and effectively.
Your organization’s future depends on it.
References
[1] Hyperproof.io. (2025, August 27).
How to Create a Cybersecurity Incident Response Plan.
[2] CrowdStrike. (2023, July 6). Incident Response Plan: Frameworks and Steps.
[3] Cynet. (2025, June 1). NIST Incident Response: 4-Step Life Cycle, Templates and Best Practices.
