
The sudden, inexplicable cessation of all activity on a computer system—the dreaded system freeze—is often more frustrating than a complete system crash or a Blue Screen of Death (BSOD).
A BSOD provides a clear bug check code, but a freeze is a moment of digital silence: a complete, temporary lockup where the screen is static and the system is utterly unresponsive [1].
This intermittent nature makes these freezes the hardest stability issues to diagnose.
They strike randomly, defying prediction and often leading users to incorrectly blame hardware.
While standard hardware checks (memory tests, temperature monitoring, disk scans) are necessary, they frequently come back clean.
Our thesis is that a systematic, software-centric approach, one that delves into the operating system’s inner workings, is absolutely required to uncover these elusive faults.

II. The Hardware-First Fallacy and Why It Fails
Before dismissing hardware entirely, a brief acknowledgment of the standard checks is due.
Diagnosis should begin with confirming the health of physical components, including running extended memory tests (e.g., MemTest86), monitoring CPU/GPU temperatures for thermal throttling, and using tools like CrystalDiskInfo to verify drive health [2].
However, when these tests pass, the real work begins.
The hardware-first fallacy is the mistaken belief that stability issues must originate from physical component failure.
This approach fails because intermittent faults are often timing-dependent, not simple breakdowns.
A freeze is frequently the result of a deadlock or resource contention at the operating system kernel level, triggered by a specific, rare sequence of events involving software, drivers, and firmware.
The hardware may be functional, but the timing of instructions sent to it causes a catastrophic stall.
III. The Silent Saboteurs: Driver and Firmware Issues
The interface between the operating system and the hardware is a fertile ground for intermittent stability problems.
Drivers and firmware, while essential, are often the silent saboteurs that introduce instability that looks like a hardware fault.
A. Driver Conflicts and Corruption
Drivers are pieces of software that allow the operating system to communicate with hardware.
A common source of freezes is a poorly written, outdated, or corrupted driver.
Insidious culprits are often non-PnP (Plug and Play) drivers, including low-level system services and virtual devices that operate with high privileges in the kernel.
To stress-test driver integrity, advanced users can employ the Driver Verifier utility (Windows).
Driver Verifier subjects drivers to stress tests, forcing adherence to strict coding standards.
If a driver violates a rule, Driver Verifier intentionally crashes the system, providing a clear bug check code that names the offending file [3].
This is crucial for isolating problematic drivers.
Furthermore, the “last update” rule is a practical diagnostic technique: if freezes began shortly after a driver update, rolling back to the previous stable version is the most immediate troubleshooting step.
B. Firmware and BIOS/UEFI Bugs
Firmware—the persistent software programmed into a hardware device—is another critical layer, including the system’s BIOS/UEFI and firmware on components like SSDs and network cards.
A common, overlooked source of intermittent freezes stems from bugs in the chipset and storage controller firmware.
A classic case study involves the Advanced Host Controller Interface (AHCI) and PCIe power management states, specifically Active State Power Management (ASPM).
If the BIOS or a driver incorrectly handles the transition of a PCIe device (e.g., an NVMe SSD) into a low-power state, the device may fail to wake up correctly, causing the system to hang until a hard reset.
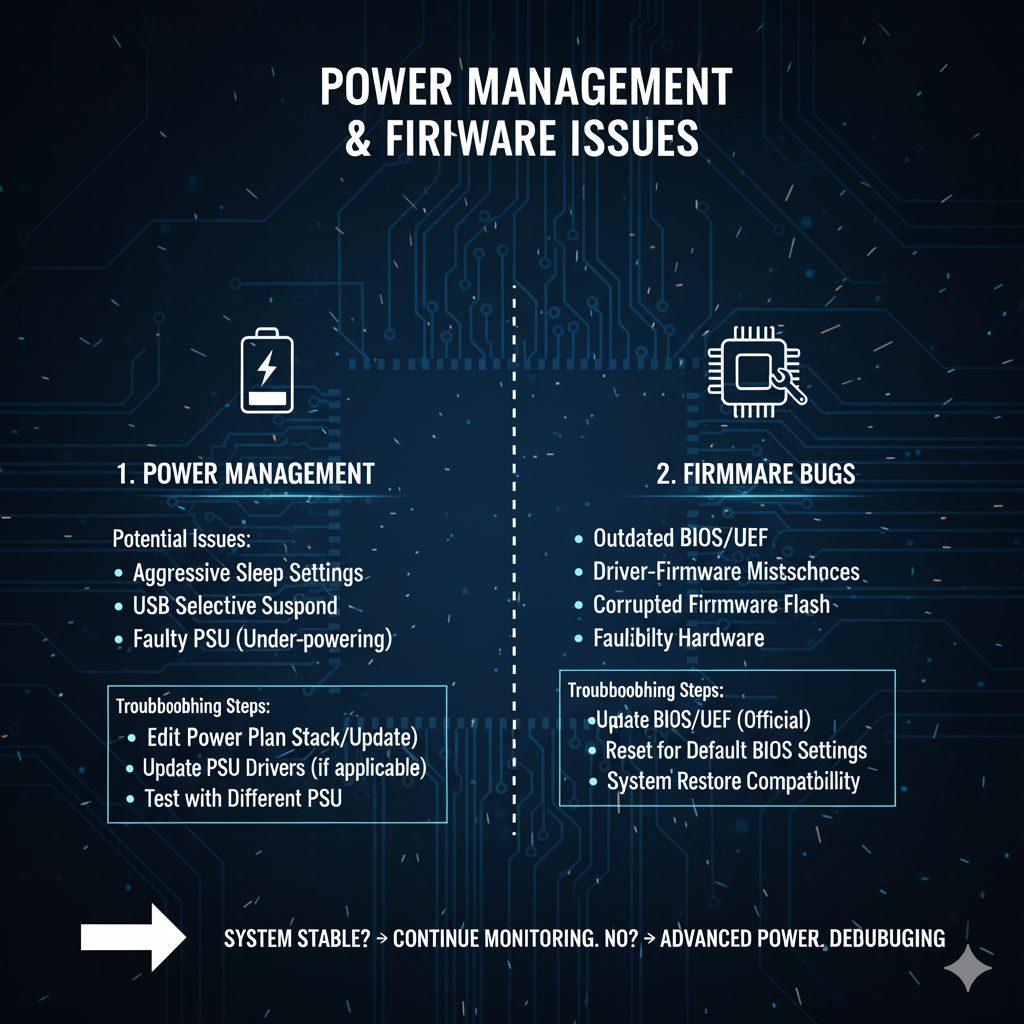
Checking for vendor-specific microcode updates for the CPU and the latest BIOS/UEFI version is paramount, as manufacturers frequently release stability fixes for these low-level timing and power management issues.
IV. Operating System and Software-Level Contention
When the system is stable at the hardware and driver level, the focus must shift to the complex dance of processes and threads within the operating system kernel.
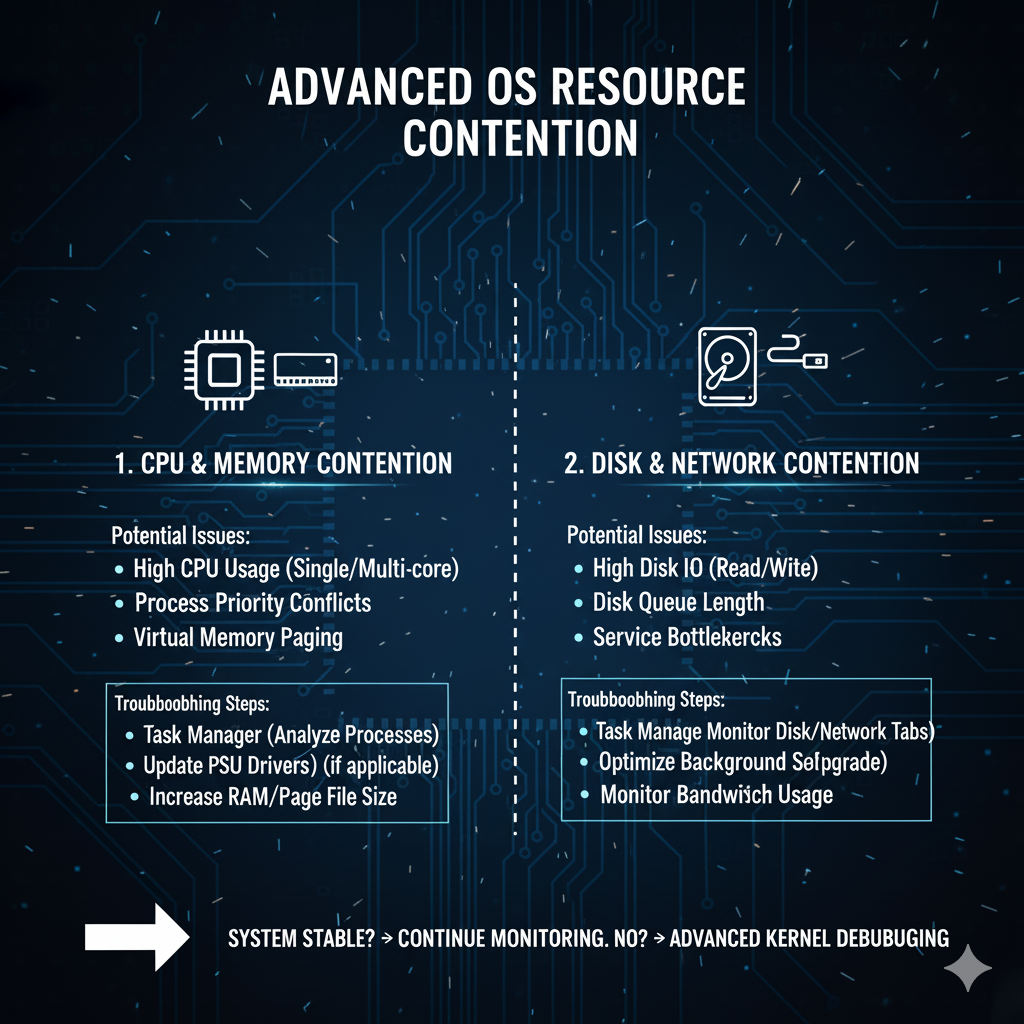
A. Resource Deadlocks and Thread Starvation
A system freeze can be a manifestation of a resource deadlock, a condition where two or more processes are waiting for each other to release a resource, resulting in a perpetual wait state.
This is a form of kernel-level contention involving synchronization primitives like spinlocks and mutexes [4].
To catch these moments, tools like Resource Monitor and Process Explorer are invaluable.
By monitoring the system in real-time, one can look for sudden, sustained spikes in I/O latency (especially disk I/O) or a process that suddenly consumes 100% of a single CPU core just moments before a freeze.
This spike often indicates the process that has entered a tight, non-yielding loop, or the resource that has become the bottleneck.
B. Corrupted System Files and Registry Hives
The integrity of the core operating system files is non-negotiable for stability.
Corruption in critical files or the Windows Registry can lead to unpredictable behavior, including intermittent freezes.
Built-in tools address this:
| Tool | Purpose | Diagnostic Value |
|---|---|---|
sfc /scannow |
System File Checker. Scans and repairs protected Windows system files. | Checks for file-level corruption that can cause system call failures. |
| DISM | Deployment Image Servicing and Management. Repairs the Windows component store. | Addresses deeper corruption in the source files used by SFC, often necessary before running SFC. |
Furthermore, the impact of third-party security software (antivirus, firewalls) cannot be overstated.
These applications inject themselves deep into the operating system’s core, intercepting system calls.

A poorly optimized or buggy security suite can introduce significant overhead and, in rare cases, cause a deadlock or race condition that results in a system freeze.
Temporarily disabling or uninstalling such software is a critical isolation step.
C. Power Management and Throttling
Aggressive power management settings, designed to save energy, can inadvertently cause system instability.
The system may enter a low-power state too quickly or fail to transition back to a high-power state efficiently, leading to a momentary stall.
In Windows, the “Minimum Processor State” setting is a common culprit.
If set too low (e.g., 5%), the CPU may aggressively downclock, and the time taken to ramp back up to full speed can manifest as a temporary freeze.
More fundamentally, investigating C-states and P-states in the BIOS is necessary.
C-states are CPU idle states, and P-states are performance states.
If the transition between these states is flawed, or if a peripheral device cannot handle the rapid power cycling, the system can hang.
This is common in modern systems where aggressive downclocking to save power causes a temporary stall when resources are suddenly demanded.
V. Advanced Diagnostic Tools and Techniques
Moving beyond basic checks requires a commitment to using professional-grade tools that capture the state of the system at the exact moment of failure.
A. The Windows Event Viewer Deep Dive
The Windows Event Viewer is the operating system’s black box recorder, and the first crucial tool for post-mortem analysis.
The key is to look at the events immediately preceding and immediately following the forced reboot, not just the time of the freeze.
A systematic approach involves filtering the System and Application logs for critical errors and warnings that occurred in the minutes leading up to the freeze.
Specific events to focus on include:
| Event Log | Event Source | Description |
|---|---|---|
| System | BugCheck |
Indicates a system crash (BSOD) occurred, even if the user only perceived a freeze. |
| System | DistributedCOM |
Often points to issues with inter-process communication or service timeouts. |
| System | disk or storahci |
High disk I/O latency or reset commands, suggesting a storage controller issue. |
| Application | Application Error | Errors in a specific application that may have triggered the resource contention. |
The event log will often contain a Warning or Error that occurred just before the system became unresponsive, pointing directly to the faulting component or service.
B. Performance Monitoring with Windows Performance Recorder (WPR) / Analyzer (WPA)
For the most elusive freezes, a continuous performance trace is the only way to capture the root cause.
The Windows Performance Recorder (WPR) and its companion, the Windows Performance Analyzer (WPA), are designed for this purpose [5].
The technique involves setting up a circular buffer trace to continuously record system activity.
When a freeze occurs, the user forces a hard reboot, and the trace file contains the data leading up to the failure.
WPA allows for deep analysis of this trace, focusing on:
- Context Switches: Identifying which threads are running and which are waiting, revealing deadlocks.
- DPC/ISR Activity: Checking for excessive Deferred Procedure Call (DPC) or Interrupt Service Routine (ISR) time, which indicates a driver monopolizing the CPU.
- Disk I/O Latency: Pinpointing the exact moment a disk operation stalls, often revealing a storage subsystem issue.
By analyzing the trace, one can identify the specific thread or process that holds a critical resource, providing a snapshot of the system’s state at the moment of the stall.
C. Kernel-Mode Debugging (The Last Resort)
When all other methods fail, kernel-mode debugging is the ultimate diagnostic technique, involving the analysis of a memory dump file created at the moment of the freeze.
- Setting up a Manual Memory Dump: This is configured in Windows to be triggered manually (e.g., right
Ctrl+Scroll Locktwice), forcing the system to write the contents of physical memory to a dump file before rebooting. - Using WinDbg: The Windows Debugger (WinDbg) analyzes the dump file. By loading symbols, WinDbg can trace the execution path of the CPU at the time of the dump.
- Interpreting Bug Check Codes: The manual dump reveals the underlying state. The debugger examines the stack trace of frozen threads and interprets common bug check codes (e.g.,
IRQL_NOT_LESS_OR_EQUAL) that were about to be triggered, pointing directly to the faulting module, often a driver file.
VI. The Systematic Troubleshooting Methodology
The key to solving intermittent freezes is not a single tool, but a disciplined, methodical approach.
Step 1: Isolate the Variable.
Reduce the system to its most basic, stable state by booting into Safe Mode or performing a Clean Boot (disabling all non-Microsoft services).
If stable, the fault lies with a third-party application or service.

For extreme cases, a fresh OS install on a separate, temporary partition is the ultimate isolation test.
Step 2: Log Everything.
Meticulous logging is essential.
Use a secondary device to record the exact time of the freeze, the applications running, and the specific action performed (e.g., “opened Chrome with 10 tabs,” “system was idle”).
This contextual data often reveals the pattern.
Step 3: Incremental Reintroduction.
Once stability is confirmed, reintroduce applications, drivers, and services one by one, or in small, logical groups.
This patient process is the only way to pinpoint the single piece of software that reintroduces the instability.
Step 4: Stress-Testing the Suspect.
After a fix, the system must be rigorously tested.
Use targeted stress-testing tools like Prime95 (CPU), FurMark (GPU), and I/O testing utilities to confirm that the fix has not only resolved the intermittent freeze but that the system is now rock-solid under maximum, sustained load.
VII. Conclusion: Stability Through Diligence
The diagnosis of intermittent system freezes is a test of patience and technical diligence.
It moves quickly beyond the simplicity of hardware tests and into the complex world of operating system kernels, drivers, and firmware.
The culprits are rarely the CPU or RAM, but rather the subtle interactions between software components—the driver that mismanages a power state, the service that enters a deadlock, or the corrupted system file that causes a critical resource to stall.
By adopting a methodical, systematic approach, leveraging advanced diagnostic tools, and meticulously logging the context of each failure, the elusive root cause can be identified and eliminated.
Stability is not a given; it is achieved through diligence and a commitment to deep-level troubleshooting.
References
- [1] Placeholder for a technical article defining system freeze vs. crash.
- [2] Placeholder for a guide on standard PC hardware diagnostics.
- [3] Placeholder for Microsoft documentation on Driver Verifier.
- [4] Placeholder for a computer science text on operating system deadlocks and synchronization.
- [5] Placeholder for Microsoft documentation on Windows Performance Toolkit (WPR/WPA).
