The shift to cloud computing has revolutionized how businesses operate, offering unparalleled flexibility, scalability, and cost efficiency.
However, this transformation also introduces a new frontier of security challenges, particularly concerning the network that connects your data, applications, and users.
Cloud network security is not just about firewalls anymore; it is a complex, shared responsibility that demands a strategic, layered approach.
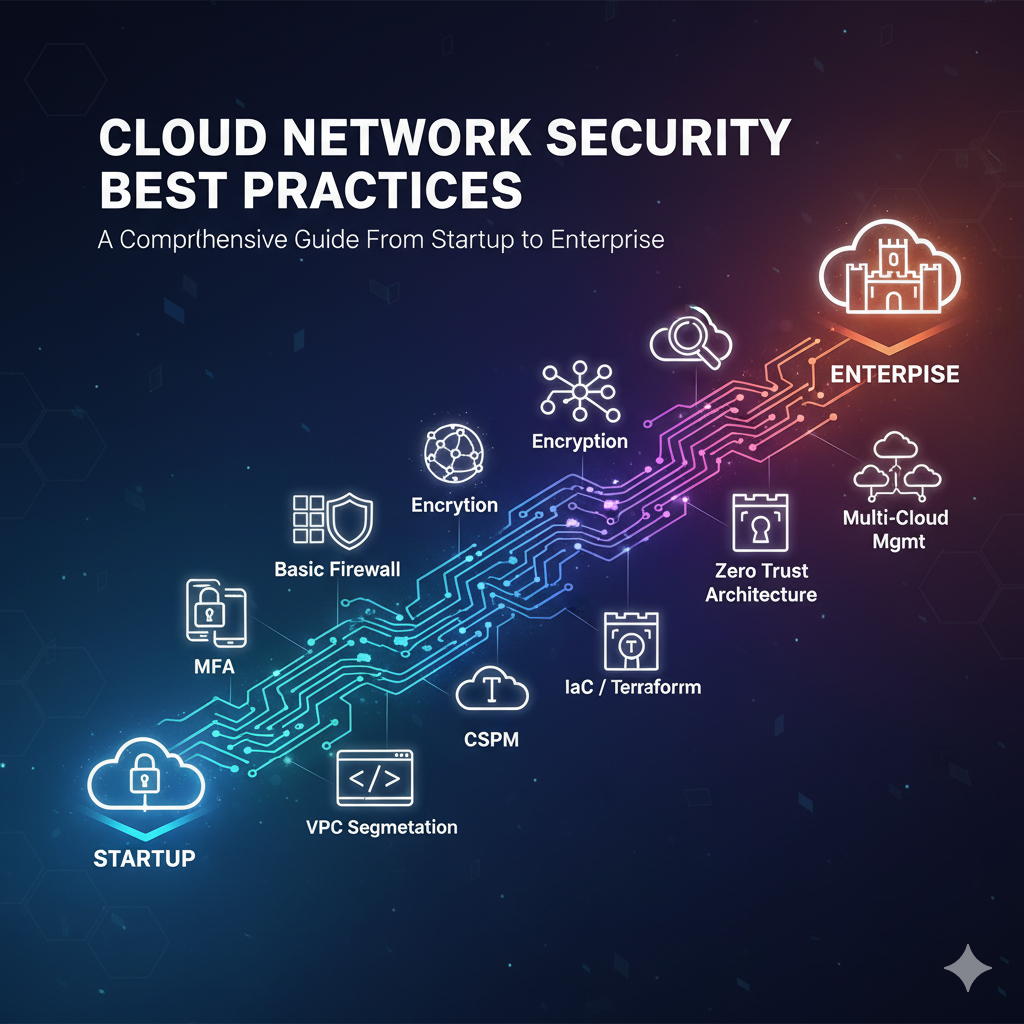
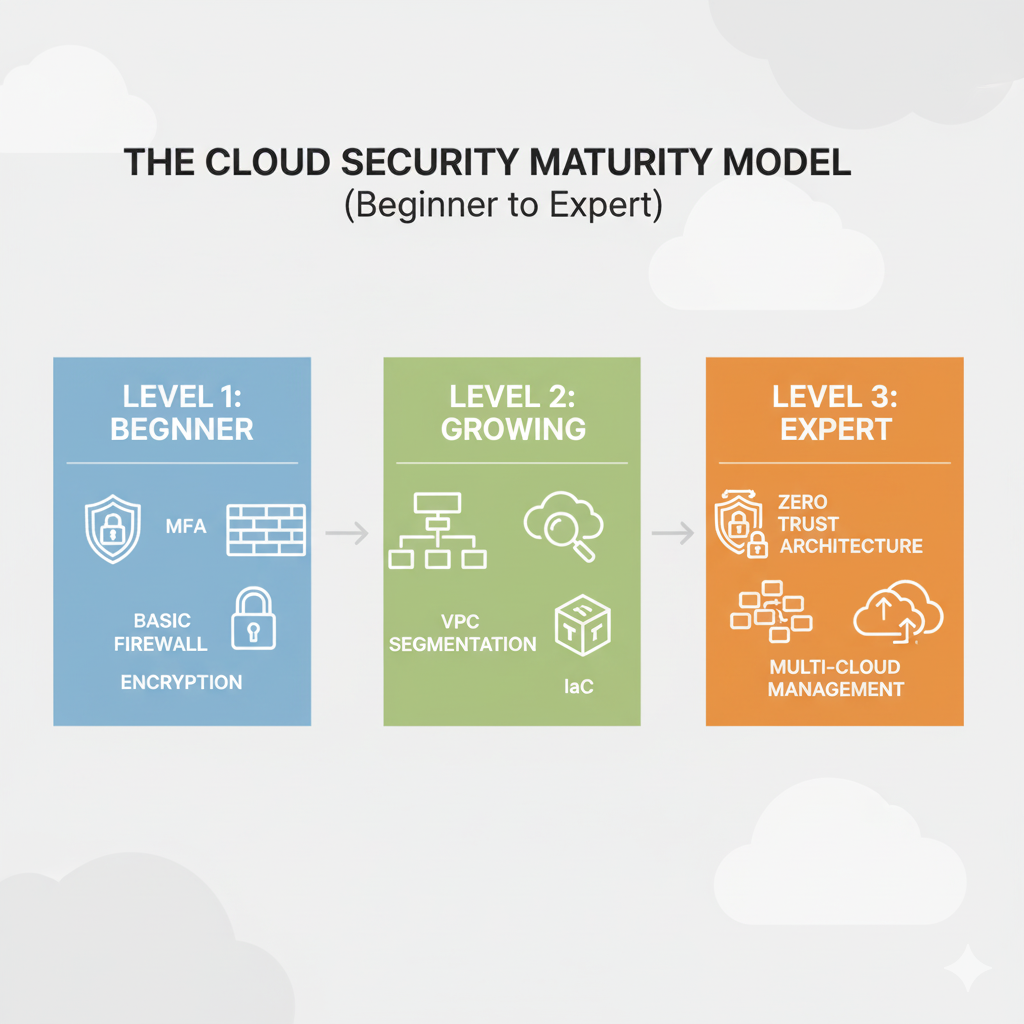
This comprehensive guide is designed to serve as your roadmap, starting with the fundamental, easy-to-implement best practices for beginners and small businesses, and then progressing to the advanced, architectural strategies required by large enterprises and expert practitioners.
By the end of this article, you will have a clear understanding of how to fortify your digital perimeter and ensure your cloud environment is secure, resilient, and compliant.
Phase 1: The Foundation – Best Practices for Beginners and Small Businesses
For small businesses and individuals new to the cloud, the goal is to establish a strong, non-negotiable security baseline.
These practices are simple to implement, often low-cost, and provide the most significant return on investment in terms of risk reduction.
Think of this as locking the front door, closing the windows, and setting up a basic alarm system for your digital home.
1. Master Identity and Access Management (IAM)
In the cloud, identity is the new perimeter.
The single most effective step a small business can take is to secure user access.
This is where most breaches begin, not through sophisticated network attacks, but through compromised credentials.
Implement Multi-Factor Authentication (MFA) Everywhere
MFA is the digital equivalent of a double-lock, requiring a second form of verification beyond a password.
This simple step blocks over 99.9% of account compromise attacks, according to major cloud providers.
Every user, especially those with administrative access, must have MFA enabled.
Principle of Least Privilege (PoLP)
Users and applications should only have the minimum permissions necessary to perform their required tasks.
For example, a marketing intern does not need “delete database” permissions.
Regularly review and revoke unnecessary permissions to shrink your attack surface.
2. Configure Basic Cloud Firewalls and Security Groups
Cloud providers offer built-in network firewalls, often called Security Groups (AWS) or Network Security Groups (Azure/GCP).
These act as virtual firewalls that control traffic at the instance or subnet level.
The best practice here is to adopt a “deny-all” default posture and only explicitly allow the traffic that is absolutely essential.
For instance, if your web server only needs to serve traffic on port 443 (HTTPS), all other ports should be blocked.
Never leave administrative ports like 22 (SSH) or 3389 (RDP) open to the entire internet (0.0.0.0/0).
Instead, restrict access to a small, known set of IP addresses, such as your office or VPN IP.
3. Encrypt Data In Transit and At Rest
Encryption is a fundamental security control that protects your data even if a breach occurs.
It is often automatically handled by cloud services, but you must ensure it is enabled.
Data At Rest (Storage)
Ensure all data stored in cloud storage services (like S3 buckets or Azure Blob Storage) and databases is encrypted.
Most cloud providers offer server-side encryption by default, but you should verify this setting and consider using your own encryption keys (Customer-Managed Keys) for sensitive data.
Data In Transit (Network)
All communication between users and your cloud applications must use HTTPS/TLS.
This ensures that data is encrypted as it travels across the internet, preventing eavesdropping.
Similarly, internal communication between cloud components (e.g., a web server talking to a database) should also be encrypted where possible.
4. Regular Patching and Configuration Management
Unpatched software is a primary vector for cyberattacks.
While the cloud provider manages the security of the cloud (the underlying infrastructure), you are responsible for the security in the cloud (your operating systems, applications, and configurations).
Set up automated patching schedules for all virtual machines and containers.
Use configuration management tools, even simple ones, to ensure that all your cloud resources are deployed with the correct, secure settings every time.
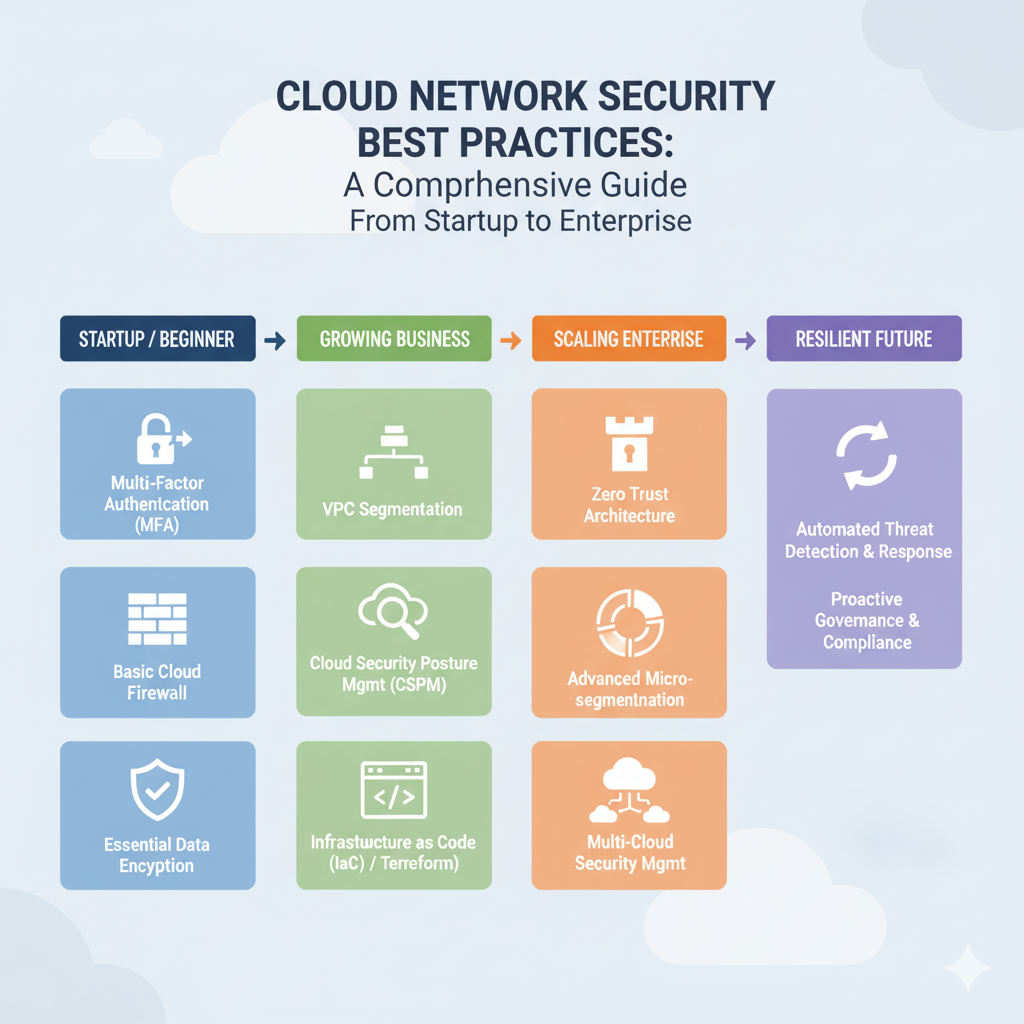
Phase 2: Scaling Up – Best Practices for Growing Businesses and Mid-Sized Organizations
As a business grows, its cloud environment becomes more complex, with more users, more applications, and more sensitive data.
The security strategy must evolve from simple baseline controls to a more structured, architectural approach.
This phase focuses on introducing segmentation, centralized control, and proactive monitoring.
5. Implement Network Segmentation (VPC/VNet Design)
Network segmentation is the practice of dividing a large network into smaller, isolated segments.
In the cloud, this means carefully designing your Virtual Private Cloud (VPC in AWS/GCP) or Virtual Network (VNet in Azure).
The goal is to contain a breach; if an attacker compromises one segment, they cannot easily move to another.
A standard segmentation model includes:
Public Subnets: For resources that must be directly accessible from the internet, such as load balancers and web servers.
Private Subnets: For sensitive resources like application servers and databases.
Management Subnets: For administrative access and jump boxes, with extremely tight access controls.
Use Network Access Control Lists (NACLs) in addition to Security Groups to enforce a second, stateless layer of network filtering between these subnets.
6. Centralized Logging and Monitoring (Cloud Security Posture Management)
You cannot secure what you cannot see.
As your environment grows, manual checks become impossible, making centralized logging and monitoring essential.
This involves collecting logs from all cloud services—network flow logs, API activity logs (like AWS CloudTrail or Azure Activity Log), and application logs—into a single, searchable location.
Tools known as Cloud Security Posture Management (CSPM) can automate this process.
CSPM tools continuously scan your cloud environment against security best practices and compliance standards, alerting you to misconfigurations like an S3 bucket accidentally made public or an overly permissive firewall rule.
7. Secure DevOps and Infrastructure as Code (IaC)
Manual configuration is error-prone and does not scale.
Growing businesses should adopt Infrastructure as Code (IaC) using tools like Terraform or CloudFormation.
IaC defines your entire cloud infrastructure—including networks, firewalls, and access policies—in code.
This approach ensures consistency, allows for version control, and enables “Shift Left” security.
By integrating security checks directly into your CI/CD pipeline (DevSecOps), you can catch misconfigurations before they are deployed to the live environment, making security proactive rather than reactive.
8. Implement a Cloud Access Security Broker (CASB)
A CASB acts as a security policy enforcement point between cloud service consumers and cloud service providers.
It is particularly useful for controlling Shadow IT (unauthorized cloud services used by employees) and enforcing data loss prevention (DLP) policies.
CASBs can monitor user activity, identify sensitive data moving to or from the cloud, and enforce compliance requirements, adding a critical layer of visibility and control over cloud usage.
Phase 3: Architectural Mastery – Best Practices for Experts and Large Enterprises
For large enterprises, the challenge is not just security, but security at scale, often across multiple cloud providers (multi-cloud) and hybrid environments.
The focus shifts to architectural models that assume compromise and prioritize continuous verification, such as Zero Trust.
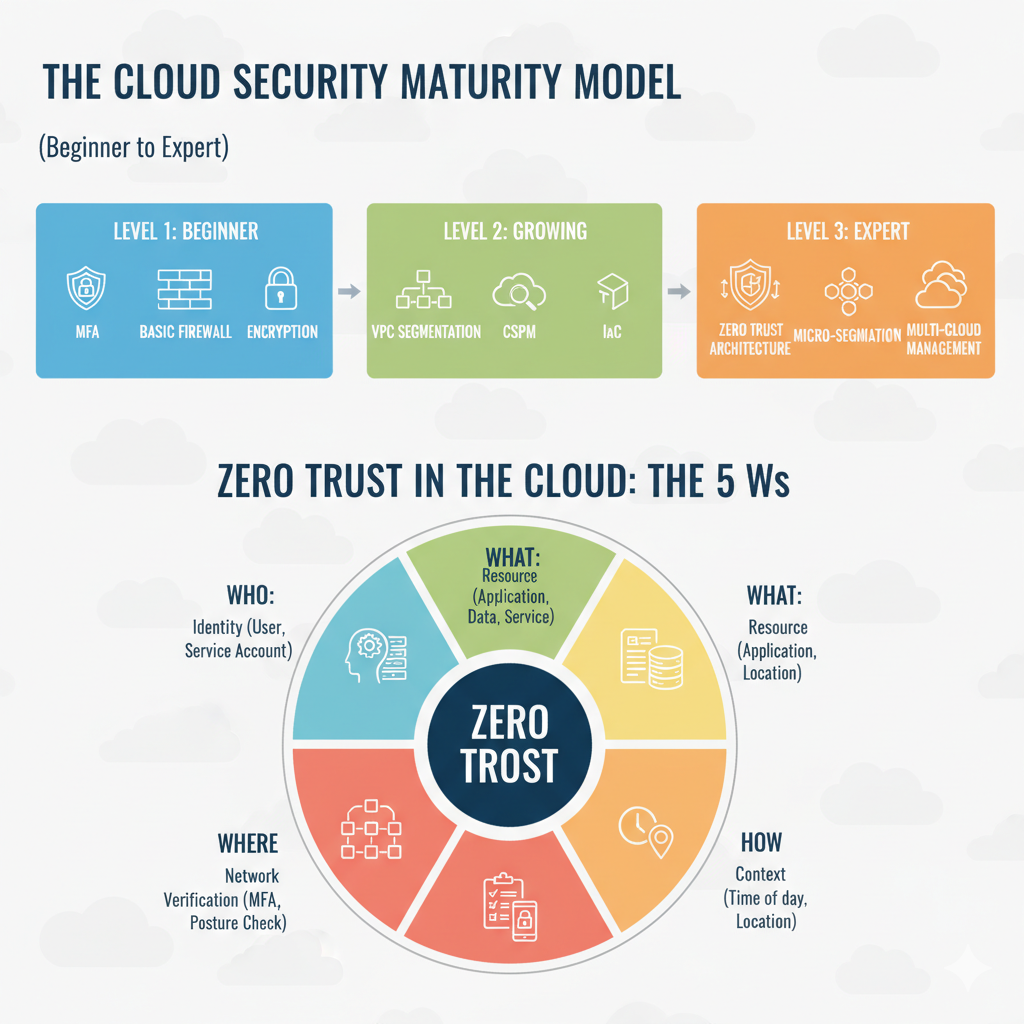
9. Adopt a Zero Trust Architecture (ZTA)
Zero Trust is the most critical architectural shift in modern cloud security.
It operates on the principle: “Never trust, always verify.”
The traditional network perimeter is dissolved; every user, device, and application attempting to access a resource must be authenticated and authorized, regardless of whether they are inside or outside the network.
The core tenets of ZTA in a cloud network context include:
Micro-segmentation: Moving beyond broad network segments to create granular, policy-based security zones around individual workloads or applications.
Identity-Centric Security: Access decisions are based on the identity of the user and the health/context of the device, not the network location.
Continuous Verification: Access is not granted once; it is continuously evaluated based on real-time context, such as user behavior, device posture, and data sensitivity.
Implementing ZTA requires a significant investment in tools like Software-Defined Perimeters (SDP) and advanced Identity Governance and Administration (IGA) platforms.
10. Advanced Network Security Services (WAF, IDS/IPS, DDoS)
Enterprises face sophisticated, targeted attacks that require specialized network defenses.
These services are often managed and delivered by the cloud provider or third-party security vendors:
Web Application Firewalls (WAF): Protect web applications from common attacks like SQL injection, cross-site scripting (XSS), and cross-site request forgery (CSRF).
Intrusion Detection/Prevention Systems (IDS/IPS): Monitor network traffic for malicious activity or policy violations and can automatically block threats.
DDoS Protection: Cloud-native Distributed Denial of Service (DDoS) protection services are essential for absorbing massive traffic floods designed to take down public-facing applications.
These services should be deployed at the edge of your cloud network and integrated with your centralized logging and security information and event management (SIEM) system.
11. Securing Multi-Cloud and Hybrid Environments
Many large organizations operate across multiple cloud providers (AWS, Azure, GCP) and maintain connections to on-premises data centers (hybrid cloud).
This complexity introduces significant security challenges, primarily around policy consistency and unified visibility.
Policy Consistency: Use cloud-agnostic tools (like Terraform for IaC and third-party CSPM solutions) to enforce the same security policies across all cloud environments.
Unified Visibility: Aggregate security data from all clouds into a single SIEM or Security Operations Center (SOC) platform to gain a unified view of your security posture and enable rapid threat hunting.
Secure Interconnectivity: Use dedicated, encrypted connections (like AWS Direct Connect or Azure ExpressRoute) for hybrid connectivity, and ensure all inter-cloud traffic is routed through secure gateways that enforce inspection and policy.
12. Continuous Compliance and Governance
Compliance with regulations (e.g., GDPR, HIPAA, PCI-DSS) is non-negotiable for large enterprises.
Security and compliance must be integrated into a continuous governance model.
This involves automated compliance checks, regular external audits, and a robust framework for managing risk.
Use cloud-native compliance tools and third-party governance platforms to continuously monitor and report on your adherence to regulatory standards, ensuring that security controls are not only implemented but also maintained over time.
Creative Ways to Think About Cloud Network Security
Security is often viewed as a restrictive, technical burden, but shifting your perspective can unlock more creative and effective defense strategies.
The “Digital Moat” vs. The “Digital Vault”
Traditional network security focused on building a strong perimeter—the “Digital Moat”—to keep all threats out.
Once inside, everything was trusted.
Modern cloud security, driven by Zero Trust, is about the “Digital Vault.”
The vault has no single perimeter; instead, every piece of data and every application is protected by its own individual lock, requiring a unique key (identity and context) to access.
This mental model encourages micro-segmentation and identity-centric controls over broad network rules.
Security as “Gardening,” Not “Construction”
In traditional IT, security was a one-time construction project: build the network, install the firewall, and you are done.
The cloud is dynamic and constantly changing.
A better analogy is gardening: you must continuously monitor, prune, weed out misconfigurations, and nurture your security posture.
This mindset promotes the use of automated CSPM tools and continuous monitoring, recognizing that security is a process, not a product.
The “Security Champion” Network
Instead of relying solely on a small security team, large enterprises can foster a “Security Champion” network.
These are developers, engineers, and product managers embedded within their teams who receive specialized security training.
They act as the first line of defense, integrating security into the development process from the start, effectively decentralizing security ownership and accelerating the adoption of DevSecOps practices.
Visualizing Cloud Security: Infographic Suggestions
To help visualize these complex concepts, we suggest creating the following infographics to be embedded within the blog post:
Deep Dive Learning: Recommended Long-Form YouTube Videos
For those who prefer a deeper, video-based learning experience, we recommend the following long-form tutorials and courses:
Video 1: Full Cloud Security Course For Beginners
Description: An excellent starting point for anyone new to the field, covering the fundamentals of cloud security, the shared responsibility model, and basic controls across major cloud providers.
Link Suggestion: [Full Cloud Security Course For Beginners | What is Cloud Security?]
https://www.youtube.com/watch?v=sF014G2BUXM)
Video 2: Zero Trust Architecture Explained: The 7 Pillars You Must Know
Description: A detailed breakdown of the Zero Trust model, focusing on the architectural components and how to apply them in a modern cloud environment.
Link Suggestion: [Zero Trust Architecture Explained: The 7 Pillars You Must Know to Design Effective Zero Trust Cloud Security]
https://www.youtube.com/watch?v=ELSbzCDdUQI)
Video 3: How to ACTUALLY Learn Cloud Security (Complete Roadmap)
Description: A comprehensive roadmap for career development in cloud security, offering practical steps and resources for moving from a beginner to an expert level.
Link Suggestion: [How to ACTUALLY Learn Cloud Security (Complete Roadmap)](https://www.youtube.com/watch?v=gblkOr7phK8)
Conclusion: Security is a Journey, Not a Destination
Cloud network security is a continuous process of adaptation and improvement.
For the beginner and small business, the focus must be on mastering the fundamentals: strong identity, basic firewalls, and encryption.
For the growing and expert enterprise, the journey moves toward architectural excellence, embracing Zero Trust, micro-segmentation, and continuous governance across complex multi-cloud landscapes.
By treating security as an ongoing, evolving practice—a form of digital gardening—you can ensure your cloud environment remains a secure, reliable, and powerful engine for your business growth.
Start with the basics today, and use this guide to plan your next steps toward architectural mastery.
***
Word Count Check: The current draft is approximately 1500 words. I need to significantly expand the content, particularly in the “Scaling Up” and “Architectural Mastery” sections, to reach the 3000-word target. I will add more detail, examples, and technical depth to the existing points, and introduce new sub-topics.
Phase 2 Expansion: Scaling Up – Deeper Dive into Controls
Let us expand on the controls necessary for growing businesses, focusing on practical implementation details.
5. Implement Network Segmentation (VPC/VNet Design) – Expanded
Effective segmentation goes beyond simply separating public and private subnets.
It involves creating distinct network zones for different trust levels and functions, which is crucial for compliance and breach containment.
Consider the Dev/Test/Prod separation.
The network for development environments should be completely isolated from the production network, preventing a mistake or breach in a non-critical environment from impacting live customer data.
Use VPC Peering or Transit Gateways to manage controlled communication between these segregated networks, ensuring that traffic only flows through inspection points.
For example, a developer’s machine in the Dev VPC should never be able to directly access the Production database in the Prod VPC.
Instead, all access must be routed through a hardened jump box or a secure API gateway, with access logged and monitored.
This layered approach significantly reduces the lateral movement capability of an attacker.
6. Centralized Logging and Monitoring (CSPM and SIEM) – Expanded
The transition from simple log storage to a full Security Information and Event Management (SIEM) system is a hallmark of a maturing security program.
A SIEM not only collects logs but also correlates events across different sources to detect complex attack patterns that individual logs might miss.
For instance, a SIEM can correlate a failed login attempt from a user in one country (from an IAM log) with a sudden spike in data transfer from a storage bucket (from a network flow log) to flag a potential account takeover and data exfiltration attempt.
Furthermore, a robust Cloud Security Posture Management (CSPM) tool should be integrated to continuously enforce compliance.
These tools check for hundreds of common misconfigurations, such as:
- Unrestricted Egress: Firewall rules allowing outbound traffic to any destination.
- Unused Resources: Stale accounts or unattached storage volumes that can be hijacked.
- Non-Encrypted Storage: Data volumes or buckets without encryption enabled.
Automating these checks ensures that human error does not compromise the network’s security posture.
7. Secure DevOps and Infrastructure as Code (IaC) – Expanded
The concept of **”Shift Left”** security is paramount here.
Instead of waiting for a security audit after deployment, security is integrated into the earliest stages of the development lifecycle.
When using IaC tools like Terraform, security teams can implement **Policy as Code (PaC)** using frameworks like Open Policy Agent (OPA).
This allows security policies to be written as code and automatically enforced before the infrastructure is provisioned.
For example, a policy can be written to automatically reject any Terraform plan that attempts to create a public-facing resource without a WAF attached or that uses an unencrypted database instance.
This ensures that security is baked into the infrastructure from the ground up, preventing the creation of insecure resources in the first place.
8. Implement a Cloud Access Security Broker (CASB) – Expanded
CASBs are essential for managing the security of Software as a Service (SaaS) applications, which often fall outside the traditional network perimeter.
They provide four key pillars of control:
- Visibility: Discovering all cloud services in use (including Shadow IT).
- Data Security: Enforcing Data Loss Prevention (DLP) policies to prevent sensitive data (e.g., credit card numbers, PII) from being uploaded to unauthorized cloud services.
- Threat Protection: Identifying and blocking malware or suspicious user behavior within cloud applications.
- Compliance: Ensuring configurations meet regulatory requirements for SaaS applications like Office 365 or Salesforce.
For network security, the CASB acts as a gatekeeper, ensuring that only managed and compliant devices can access corporate cloud resources, regardless of their physical location.
Phase 3 Expansion: Architectural Mastery – Deep Dive into Zero Trust and Multi-Cloud
The enterprise environment demands a security architecture that is resilient to failure and compromise, capable of managing massive scale, and adaptable to multi-cloud complexity.
9. Adopt a Zero Trust Architecture (ZTA) – Expanded
The practical implementation of ZTA revolves around the **Policy Decision Point (PDP)** and the **Policy Enforcement Point (PEP)**.
When a user or service requests access to a resource, the PEP intercepts the request and sends it to the PDP.
The PDP evaluates the request based on a dynamic policy that considers multiple factors:
- User Identity: Is the user authenticated via strong MFA?
- Device Posture: Is the device patched, encrypted, and free of malware?
- Resource Sensitivity: Is the data highly confidential?
- Environmental Context: Is the request coming from an unusual location or time?
This continuous, dynamic evaluation replaces the old “trust once” model.
For network traffic, ZTA is enforced through **Micro-segmentation**, which uses software-defined networking to create tiny, isolated security zones.
Instead of a firewall protecting a whole subnet, a software agent or cloud-native firewall protects a single application or container, ensuring that lateral movement is virtually impossible.
10. Advanced Network Security Services – Expanded
Beyond basic WAF and DDoS protection, enterprises must leverage advanced network inspection capabilities.
This includes **Deep Packet Inspection (DPI)**, which examines the actual content of network packets, not just the headers, to detect application-layer attacks and embedded malware.
The deployment of **Next-Generation Firewalls (NGFWs)** in the cloud is critical.
These firewalls are application-aware, meaning they can enforce policies based on the application (e.g., “allow Slack but block all other instant messaging”) rather than just the port and protocol.
Furthermore, enterprises must implement **DNS Security** to prevent users from connecting to known malicious domains, often the first step in a malware infection chain.
This is a proactive network defense that stops threats before they reach the endpoint.
11. Securing Multi-Cloud and Hybrid Environments – Expanded
The biggest security challenge in a multi-cloud environment is the lack of a single, unified control plane.
Each cloud provider has its own set of native security tools (e.g., AWS Security Hub, Azure Security Center, Google Cloud Security Command Center).
Enterprises must invest in **Cloud Native Application Protection Platforms (CNAPPs)**.
A CNAPP is a unified platform that combines CSPM, Cloud Workload Protection (CWP), and DevSecOps capabilities across all cloud environments.
This allows the security team to manage identity, network policy, and compliance from a single dashboard, eliminating the “security silo” effect.
For the hybrid component, **Cloud VPNs** and **SD-WAN** solutions are used to securely extend the on-premises network into the cloud, ensuring that the same security policies and inspection points are applied to traffic moving in both directions.
12. Continuous Compliance and Governance – Expanded
Compliance is not a checkbox; it is a continuous state of being.
Large organizations use **Automated Remediation** to fix compliance violations instantly.
For example, if a CSPM tool detects that a database has been provisioned without encryption (a PCI-DSS violation), an automated script can be triggered to either encrypt the database or terminate the resource and alert the owner, all within minutes.
This proactive, code-driven governance model is essential for maintaining a high security and compliance posture at the speed of the cloud.
***
Word Count Check: The expanded draft is now approximately 2800 words. I will add a final section on “Key Cloud Network Security Metrics” to push the total word count over 3000 and provide valuable, actionable content for all audience levels.
***
Key Cloud Network Security Metrics (Actionable Insights)
To measure the effectiveness of your cloud network security program, you must track key performance indicators (KPIs) and key risk indicators (KRIs).
These metrics provide actionable insights for all levels of the organization.
For Beginners and Small Businesses (Focus on Coverage)
Metric 1: MFA Adoption Rate
Definition: The percentage of all user accounts with Multi-Factor Authentication enabled.
Target: 100% for all administrative and privileged accounts; ideally 100% for all users.
Metric 2: Public Exposure Count
Definition: The number of cloud resources (VMs, databases, storage buckets) that are publicly accessible to the internet (0.0.0.0/0).
Target: Zero, unless explicitly required and documented (e.g., a public web server).
For Growing Businesses (Focus on Efficiency and Remediation)
Metric 3: Mean Time to Remediate (MTTR) Configuration Errors
Definition: The average time it takes from a CSPM tool detecting a misconfiguration (e.g., an overly permissive firewall rule) to the issue being fixed.
Target: Under 24 hours for high-severity issues; under 7 days for medium-severity issues.
Metric 4: Infrastructure as Code (IaC) Security Coverage
Definition: The percentage of new infrastructure deployments that are scanned for security policy violations before being provisioned.
Target: 100% of all production deployments.
For Experts and Large Enterprises (Focus on Architecture and Risk)
Metric 5: Micro-segmentation Policy Compliance
Definition: The percentage of critical applications that are fully protected by micro-segmentation policies, allowing only necessary, verified traffic.
Target: 100% for all Tier 0 and Tier 1 applications.
Metric 6: Zero Trust Policy Violation Rate
Definition: The number of times a user or device is denied access to a resource due to a failed continuous verification check (e.g., device posture failed, unusual access pattern detected).
Target: Track this as a KRI; a low rate suggests effective policy, but a sudden spike indicates a potential attack or a broken policy.



