“Security is not just a feature, it’s an assumption. Your customers assume you’re secure. You have to prove it.”
– Anonymous
In the relentless landscape of cyber threats, securing applications is paramount. 🔐
Organizations are constantly seeking robust frameworks and standards to guide their cybersecurity efforts, especially concerning application security.
Two prominent contenders in this arena are the ISO 27001 standard and the NIST Cybersecurity Framework (CSF).
While both aim to enhance information security, they approach the challenge from different perspectives, catering to distinct organizational needs and regulatory environments. 🌍
Understanding the nuances between ISO 27001 and NIST CSF is crucial for any organization striving to build and maintain secure applications.
This comprehensive blog post will delve deep into each framework, comparing their methodologies, benefits, and how they can be applied, or even combined, to create a formidable application security posture. 🛡️
Understanding the Need for Security Frameworks in Application Security
Applications are the primary interface through which users interact with data and services. 💻
Consequently, they are a prime target for cyber attackers seeking to exploit vulnerabilities, steal data, or disrupt services.
Without a structured approach, securing complex applications becomes an ad-hoc, reactive, and ultimately ineffective endeavor. 😩
Security frameworks provide:
- Structured Guidance: A roadmap for identifying, assessing, and mitigating risks.
- Comprehensive Coverage: Ensuring no critical security aspects are overlooked.
- Consistency: A uniform approach to security across different projects and teams.
- Measurability: Metrics to track security posture improvements over time.
- Compliance: Helping meet legal, regulatory, and contractual obligations.
For application security specifically, these frameworks help embed security into the entire Software Development Lifecycle (SDLC), promoting secure coding practices, rigorous testing, and robust deployment strategies. 🚀
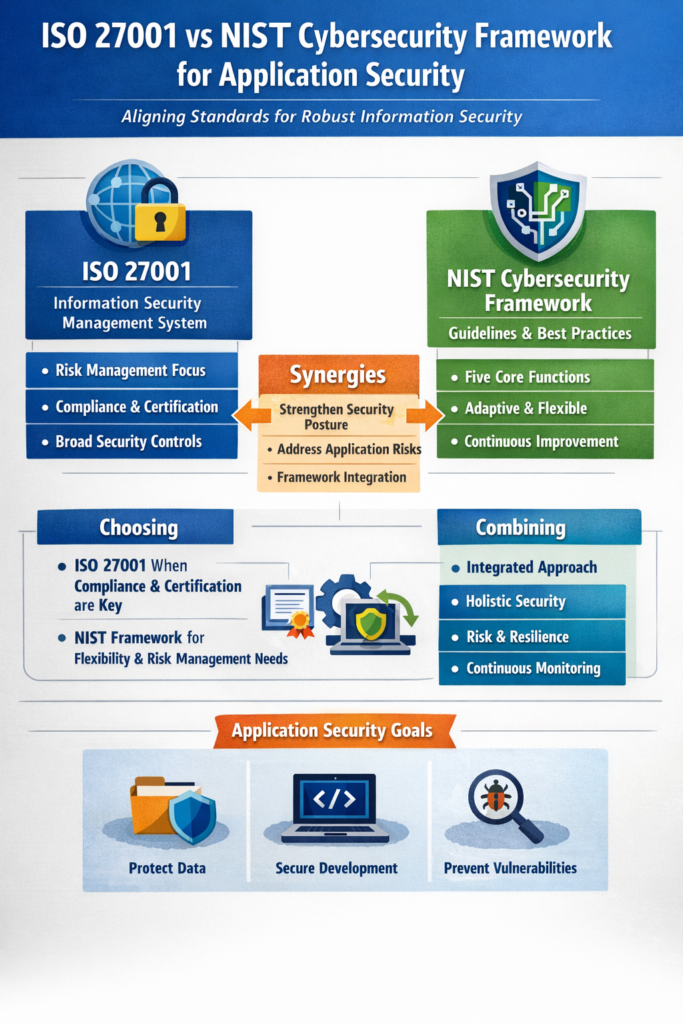
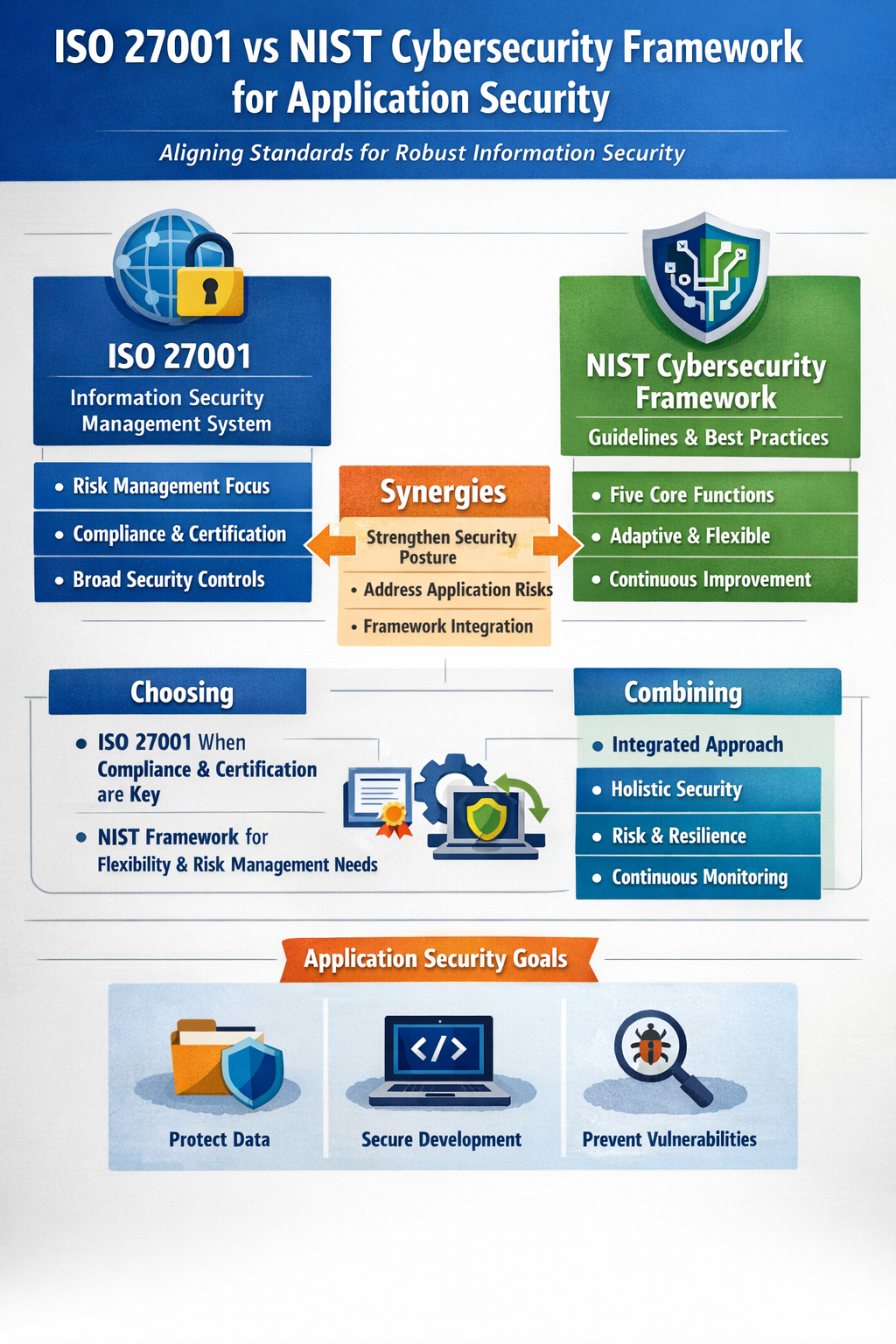
ISO 27001: The Global Standard for Information Security Management
ISO 27001 is an internationally recognized standard that specifies the requirements for establishing, implementing, maintaining, and continually improving an Information Security Management System (ISMS). 🌐
It’s part of the ISO/IEC 27000 family of standards, which provides best practice recommendations on information security management.
Key Characteristics of ISO 27001
- Management System Focused: ISO 27001 is about implementing a system to manage information security risks, not just a list of controls. It requires a top-down, management-driven approach.
- Certifiable: Organizations can achieve formal certification by an accredited third-party auditor, demonstrating their adherence to the standard. This provides external validation and builds trust. 🏅
- Risk-Based Approach: The core of ISO 27001 is a systematic risk assessment process. Organizations identify information assets, assess threats and vulnerabilities, and then determine appropriate controls based on their specific risk appetite.
- Annex A Controls: While the main body of the standard outlines ISMS requirements, Annex A provides a comprehensive list of 114 security controls categorized into 14 domains (e.g., Access Control, Cryptography, Supplier Relationships). Organizations select relevant controls based on their risk assessment and business context. 📋Learn more about ISO 27001 from ISO.
- Continuous Improvement: It follows the Plan-Do-Check-Act (PDCA) cycle, emphasizing continuous monitoring, review, and improvement of the ISMS.
ISO 27001 and Application Security
Within ISO 27001, application security is addressed through several controls in Annex A, particularly in domains like:
- A.12 Operations Security: Covers procedures for secure operation, vulnerability management, and audit logging related to applications.
- A.14 System Acquisition, Development and Maintenance: This is highly relevant, covering secure development policies, secure system engineering principles, secure development environments, system testing, and acceptance.It essentially mandates a Secure Software Development Lifecycle (SSDLC) within the ISMS. 💡
- A.9 Access Control: Addresses access rights to applications and application data.
- A.10 Cryptography: Specifies requirements for cryptographic controls within applications to protect data in transit and at rest.
- A.16 Information Security Incident Management: Pertains to how security incidents related to applications are managed and responded to.
NIST Cybersecurity Framework (CSF): A Flexible Approach to Risk Management
The National Institute of Standards and Technology (NIST) Cybersecurity Framework (CSF) is a voluntary framework developed by the U.S. government, primarily for critical infrastructure organizations, but widely adopted globally. 🇺🇸
It provides a high-level, flexible structure to manage and reduce cybersecurity risks.
Key Characteristics of NIST CSF
- Framework Core: The CSF is organized into five high-level, concurrent functions: Identify, Protect, Detect, Respond, and Recover. These functions provide a strategic view of an organization’s management of cybersecurity risk.Explore the NIST Cybersecurity Framework.
- Framework Tiers: Tiers (Partial, Risk-Informed, Repeatable, Adaptive) describe the maturity of an organization’s cybersecurity risk management practices. They help organizations understand where they are and where they want to go.
- Implementation Profiles: Profiles help organizations align their existing cybersecurity activities with the CSF functions and categories, identifying opportunities for improvement based on business requirements and risk appetite.
- Informative References: Unlike ISO 27001’s prescriptive Annex A, the NIST CSF is designed to be highly adaptable.It doesn’t define specific controls but rather maps to a wide array of existing standards and guidelines, including ISO 27001, COBIT, and NIST’s own special publications (like NIST SP 800-53). 📚
- Voluntary and Flexible: The CSF is voluntary and non-prescriptive, allowing organizations to tailor its implementation to their unique risk environment and resources.
NIST CSF and Application Security
Application security is woven throughout the NIST CSF functions:
- Identify (ID):
- Asset Management (ID.AM): Identifying applications, their components, and data flows.
- Risk Assessment (ID.RA): Assessing application-specific threats and vulnerabilities (e.g., OWASP Top 10).
- Governance (ID.GV): Establishing policies for secure application development and deployment.
- Protect (PR):
- Identity Management and Access Control (PR.AC): Implementing strong authentication and authorization within applications.
- Data Security (PR.DS): Encrypting sensitive data handled by applications, ensuring data integrity.
- Protective Technology (PR.PT): Utilizing WAFs (Web Application Firewalls), secure coding practices, and secure development environments.Veracode offers valuable resources on application security.
- Awareness and Training (PR.AT): Training developers on secure coding.
- Detect (DE):
- Detection Processes (DE.DP): Implementing application security monitoring, logging, and intrusion detection for application layer attacks.
- Security Continuous Monitoring (DE.CM): Real-time monitoring of application behavior.
- Respond (RS):
- Response Planning (RS.RP): Developing application-specific incident response plans.
- Analysis (RS.AN): Analyzing application security incidents to understand root causes and impact.
- Recover (RC):
- Recovery Planning (RC.RP): Planning for application recovery and restoration after a security event.
ISO 27001 vs. NIST CSF: A Head-to-Head Comparison
While both frameworks aim for robust cybersecurity, their fundamental differences dictate their optimal use cases. 🤔
| Feature | ISO 27001 | NIST CSF |
|---|---|---|
| Type | International Standard (Certifiable) | Framework (Voluntary Guidance) |
| Focus | Establishing an ISMS (Management System) | Managing and Reducing Cybersecurity Risk |
| Prescriptiveness | More prescriptive (Annex A controls) | Less prescriptive, adaptable, references existing standards |
| Target Audience | Any organization globally seeking formal certification | Primarily U.S. critical infrastructure, widely adopted by diverse organizations for risk management |
| Primary Driver | Achieve certification, demonstrate compliance, market advantage | Improve risk management, communicate risk, flexibility |
| Cost of Implementation | Potentially higher due to certification process and strict ISMS requirements | Generally lower, as no formal certification is required, flexible implementation |
| Outcome | Certified ISMS, demonstrable compliance with an international standard | Improved cybersecurity risk management posture, tailored to specific needs |
Choosing the Right Framework for Application Security
The “better” framework depends entirely on your organization’s specific context, goals, and regulatory environment. 🎯
Choose ISO 27001 if:
- You need formal certification: For contractual obligations, regulatory requirements, or to demonstrate security assurance to clients globally. 🌍
- You operate internationally: It’s a globally recognized standard, making it ideal for international business. ✈️
- You want a comprehensive management system: ISO 27001 drives a holistic approach to information security across the entire organization, not just technology. 🧠
- You prefer a more structured, prescriptive approach: Annex A provides a detailed list of controls to consider. 📌
Choose NIST CSF if:
- You need flexibility and adaptability: It’s highly customizable to your specific risk profile and existing security programs. 🤸
- You are in the U.S. critical infrastructure sector: It was initially designed for this purpose and is often mandated or highly recommended. 🏭
- You want to improve your cybersecurity risk management: Its five functions provide an excellent framework for understanding, assessing, and improving risk posture. 📈
- You want to leverage existing controls and standards: Its informative references allow you to map your current efforts to the framework. 🔗
Can They Be Used Together? The Synergistic Approach
Absolutely! Many organizations find significant value in integrating aspects of both frameworks. In fact, they are highly complementary. 🤝
Think of it this way:
- ISO 27001 provides the “what” and the “how”: It tells you what type of ISMS you need and gives a list of controls (Annex A) to consider as you build it. 🏗️
- NIST CSF provides the “why” and a communication tool: It helps you understand and communicate your cybersecurity risk at a high level (Identify, Protect, Detect, Respond, Recover) and can guide you in prioritizing your ISO 27001 control implementation based on your risk profile. 🗣️
Here’s how they can work together, particularly for application security:
- Use NIST CSF to define your current and target cybersecurity profile: Map your existing application security controls and processes to the CSF functions and categories. This helps identify gaps and prioritize improvements. 🗺️
- Utilize ISO 27001’s ISMS for governance and structure: Implement the formal ISMS as required by ISO 27001 to manage your overall information security, including application security risks. This provides the auditable framework. 🏛️
- Map NIST CSF to ISO 27001 Annex A controls: When selecting controls from Annex A for your Statement of Applicability, you can use the NIST CSF’s detailed categories and subcategories to inform which ISO controls are most relevant and how to implement them for application security. This ensures that the chosen controls align with a comprehensive risk management strategy. 🔄
- Leverage NIST SP 800-53 for detailed controls: If ISO 27001 Annex A controls feel too high-level, NIST SP 800-53 offers a much more granular set of security controls that can be implemented to satisfy ISO 27001 requirements, especially for technical aspects of application security. 📖
- Continuous Improvement: The PDCA cycle of ISO 27001 perfectly complements the continuous improvement nature of the NIST CSF tiers. As you improve your application security posture (guided by CSF), you also improve your ISMS (as per ISO 27001). 📈
“You can’t buy security. You build it, one decision at a time.”
– Deming’s Principle adapted for cybersecurity
Application Security Best Practices with Framework Guidance
Regardless of which framework (or combination) you choose, certain application security best practices remain universal: 🌟
- Secure SDLC (SSDLC): Integrate security into every phase of software development, from requirements gathering and design (Threat Modeling) to coding (SAST, secure coding standards), testing (DAST, Pen Testing), and deployment. 🏗️
- Threat Modeling: Proactively identify and assess potential threats to your application’s architecture and design. This is a critical activity explicitly supported by both frameworks in their risk management components. 🔍
- Input Validation and Output Encoding: Protect against common injection attacks (SQL Injection, XSS) by rigorously validating all user inputs and properly encoding outputs. ⌨️
- Strong Authentication and Authorization: Implement robust authentication mechanisms (e.g., MFA) and enforce the principle of least privilege for access control within applications. 🔑
- Secure API Design: Protect APIs with authentication, authorization, rate limiting, and input validation, as APIs are increasingly common attack vectors. 🔗
- Data Encryption: Encrypt sensitive data both in transit (TLS/SSL) and at rest (disk encryption, database encryption) within your applications. 🔐
- Regular Security Testing: Continuously perform SAST, DAST, IAST, and periodic penetration testing to identify and remediate vulnerabilities. 🧪
- Vulnerability Management: Establish a process to regularly scan for known vulnerabilities in libraries, frameworks, and third-party components (SCA – Software Composition Analysis). Promptly patch and update. 🩹
- Logging and Monitoring: Implement comprehensive logging of security-relevant events and actively monitor these logs for suspicious activities and potential breaches. 📊
- Incident Response Plan: Develop and regularly test a specific incident response plan for application security incidents. 🚨
- Security Awareness Training: Educate developers, QA, and operations teams on secure coding principles and common application security vulnerabilities. 🧑💻
- Cloud Application Security: For cloud-native or cloud-hosted applications, leverage cloud-native security tools and ensure configurations align with cloud security best practices (e.g., CSPM – Cloud Security Posture Management). ☁️
The Future of Application Security and Frameworks
The cybersecurity landscape is dynamic, and so too are the frameworks guiding it. 🔄
Expect to see continued evolution in both ISO 27001 and NIST CSF to address emerging threats like:
- AI/ML Security: How to secure AI/ML models and applications that use them. 🤖
- Supply Chain Security: Enhanced focus on securing the software supply chain, including third-party components and open-source software. 📦
- Zero Trust Architectures: Frameworks will continue to emphasize Zero Trust principles, moving away from perimeter-based security to verify every user, device, and application request. 🌐
- DevSecOps Integration: Deeper integration of security tools and automated checks within the CI/CD pipeline, making security an intrinsic part of agile development. ⚙️
These evolving challenges will only underscore the importance of having a robust, adaptable, and comprehensive security strategy informed by leading frameworks.
Conclusion
Both ISO 27001 and the NIST Cybersecurity Framework offer invaluable guidance for building and maintaining strong application security. 💪
ISO 27001 provides a certifiable, internationally recognized management system that drives a comprehensive, risk-based approach to information security across the entire organization. It’s ideal for those seeking formal validation and a structured ISMS. 🏅
NIST CSF, on the other hand, offers a flexible, risk-focused framework that helps organizations understand, assess, and improve their cybersecurity posture with adaptable profiles and informative references. It’s excellent for those prioritizing adaptable risk management and communication. 📈
The choice between them, or the decision to combine them, depends on your organization’s unique goals, regulatory landscape, and security maturity. By leveraging the strengths of either or both, organizations can significantly fortify their application security, protect critical data, and build trust in an increasingly vulnerable digital world. 🌟
