“The only truly secure system is one that is powered off, cast in a block of concrete, and sealed in a lead-lined room with armed guards – and even then, I have my doubts.”
– Gene Spafford
In today’s interconnected world, where cyber threats lurk around every digital corner, securing your network is no longer an option but a critical imperative. 🤓
Traditional perimeter-based security models are increasingly proving insufficient against sophisticated attacks.
This is where advanced networking concepts like network segmentation come into play, offering a robust and proactive approach to safeguarding your digital assets. 🛡️
This comprehensive guide will delve into the intricacies of network segmentation, exploring its fundamental principles, diverse implementations, and the unparalleled benefits it brings to organizations of all sizes. 💡
What Exactly is Network Segmentation?
At its core, network segmentation is the practice of dividing a computer network into smaller, isolated subnetworks or segments.
Think of it like creating watertight compartments on a ship. 🚢
If one compartment floods, the entire ship isn’t compromised; only that specific section is affected.
Similarly, in a segmented network, if a security breach occurs in one segment, the damage is contained, preventing attackers from easily moving laterally to other parts of the network.
This isolation is achieved through various mechanisms, including firewalls, VLANs (Virtual Local Area Networks), and more advanced software-defined networking (SDN) solutions.
The primary goal is to limit the blast radius of an attack and enhance overall network security posture. 🔒
It’s about creating granular control over traffic flow and access, ensuring that only authorized users and devices can communicate with specific resources.
Why is Network Segmentation So Crucial?
The reasons for implementing network segmentation are compelling and multifaceted. 🌟
In an era of increasing cyber threats, it’s no longer enough to have a strong outer shell; you need robust internal defenses too.
Here’s why it has become a cornerstone of modern cybersecurity strategies:
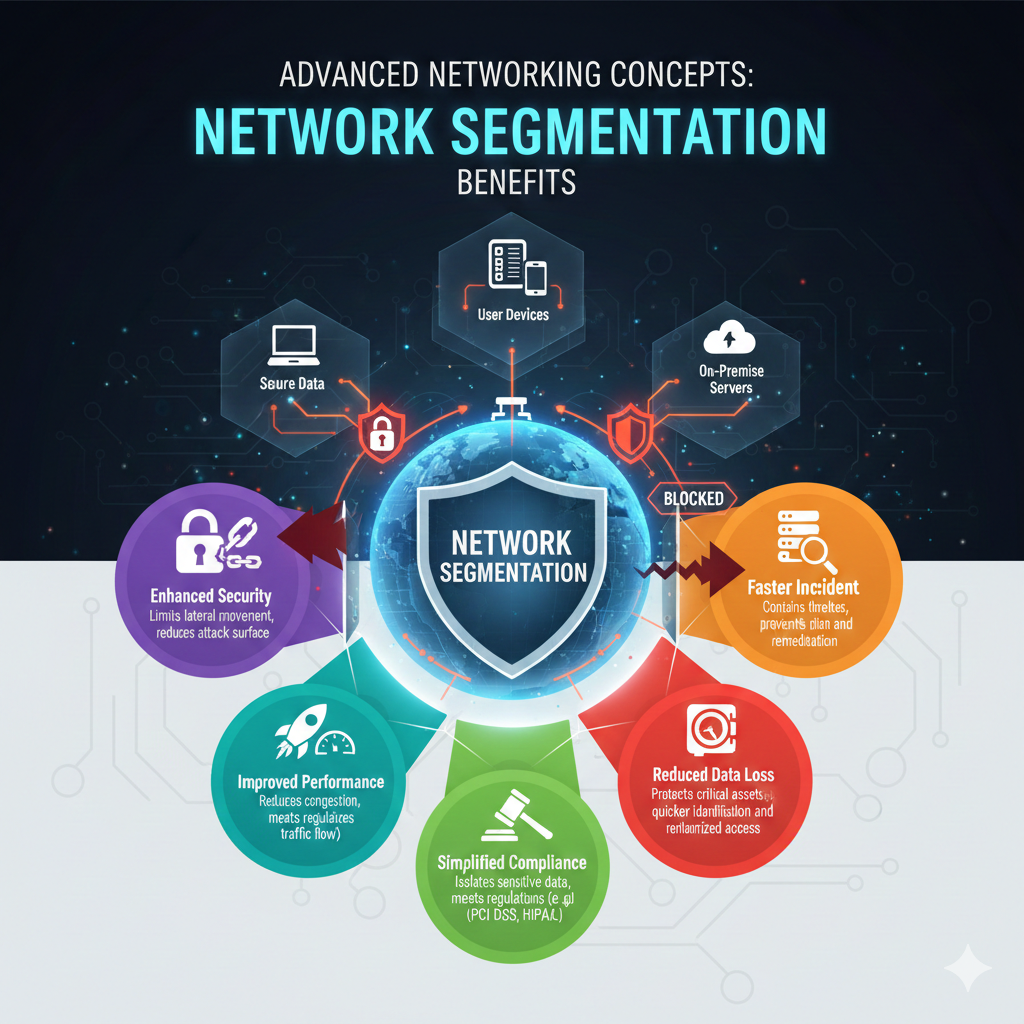
- Enhanced Security: This is arguably the most significant benefit. By isolating sensitive data and critical systems, segmentation dramatically reduces the attack surface and limits the lateral movement of threats.
- Improved Performance: By reducing broadcast domains and localizing traffic, segmentation can improve network performance and reduce congestion. 🚀
- Simplified Compliance: Many regulatory frameworks (like HIPAA, PCI DSS, GDPR) mandate strict controls over data access. Segmentation helps organizations meet these compliance requirements by isolating sensitive data environments.
- Better Incident Response: When a breach occurs, segmentation makes it easier to identify the affected area, contain the threat, and remediate the issue without impacting the entire network.
- Reduced Risk of Data Loss: By creating barriers between different data types and user groups, the risk of unauthorized data access and subsequent loss is significantly minimized.
“Security is not a product, but a process.”
– Bruce Schneier
Types of Network Segmentation
Network segmentation isn’t a one-size-fits-all solution; it comes in various forms, each suited for different organizational needs and complexities. 🧩
Understanding these types is key to implementing an effective strategy.
1. Traditional Segmentation (VLANs and Firewalls)
This is the most common and foundational approach to network segmentation.
It involves using VLANs and physical firewalls to divide the network.
- Virtual Local Area Networks (VLANs): VLANs logically group devices together, regardless of their physical location on the network.Devices within the same VLAN can communicate as if they were on the same physical network, while communication between different VLANs requires a router or a Layer 3 switch, typically protected by a firewall.
- Firewalls: Firewalls act as gatekeepers, controlling inbound and outbound network traffic based on predefined security rules.By placing firewalls between different network segments, organizations can enforce strict access policies and prevent unauthorized communication.
2. Microsegmentation
Microsegmentation takes network segmentation to a much finer granularity. 🔬
Instead of segmenting the network into broad zones, microsegmentation isolates individual workloads or applications within a data center or cloud environment.
It achieves this by applying security policies at the workload level, often using software-defined networking (SDN) or host-based firewalls.
Each application or server gets its own security perimeter, effectively creating a “zero-trust” environment where no entity is inherently trusted.
This significantly limits the lateral movement of threats, even if an attacker gains access to one workload.
3. Software-Defined Segmentation (SDN)
Software-Defined Networking (SDN) offers a more agile and programmatic approach to network segmentation. 💻
With SDN, network control is decoupled from the hardware, allowing administrators to manage network infrastructure and security policies centrally through software.
This enables the dynamic creation and enforcement of segmentation policies, making it easier to adapt to changing business needs and security requirements.
SDN-based segmentation is particularly beneficial in large, complex environments and cloud deployments.
4. Cloud Segmentation
As organizations increasingly move to the cloud, cloud segmentation has become vital. ☁️
Cloud providers offer various tools and services to implement segmentation within their environments, such as Virtual Private Clouds (VPCs), security groups, and network access control lists (NACLs).
Implementing effective segmentation in the cloud is crucial for securing cloud workloads, data, and applications, aligning with the shared responsibility model of cloud security.
Key Benefits of Network Segmentation
The advantages of implementing a well-designed network segmentation strategy are far-reaching, impacting various aspects of an organization’s IT operations and security posture. 💪
| Benefit Category | Description |
|---|---|
| Improved Security Posture | Limits the spread of malware and cyberattacks, reduces the attack surface, and enforces granular access control. |
| Enhanced Compliance | Facilitates meeting regulatory requirements by isolating sensitive data and systems. |
| Optimized Network Performance | Reduces network congestion and broadcast traffic, leading to more efficient network operations. |
| Faster Incident Response | Enables quicker identification, containment, and remediation of security incidents. |
| Reduced Risk of Data Loss | Protects critical data by preventing unauthorized access and exfiltration. |
| Greater Operational Agility | Allows for easier testing, deployment, and management of applications and services. |
Examples of Network Segmentation in Action
To illustrate the practical applications and benefits, let’s look at a few common scenarios where network segmentation proves invaluable: 🌍
- Isolating Guest Networks: A common and essential use case. Guest Wi-Fi networks are segmented from the corporate network, preventing visitors from accessing sensitive internal resources.This is typically achieved using VLANs and firewalls.
- PCI DSS Compliance: Organizations handling credit card data must comply with PCI DSS.Network segmentation helps isolate the Cardholder Data Environment (CDE) from the rest of the network, significantly reducing the scope of compliance and the risk of a breach.
This often involves a combination of VLANs, firewalls, and strict access controls.
- Separating Production and Development Environments: Development environments can sometimes be less secure or introduce vulnerabilities.Segmenting them from production systems prevents potential compromises in development from impacting live, mission-critical applications.
- Securing Critical Infrastructure (OT/ICS): In industrial environments, Operational Technology (OT) and Industrial Control Systems (ICS) are increasingly connected to IT networks.Rigorous segmentation is vital to protect these critical systems from cyberattacks that could have severe physical consequences.
This is where specialized industrial firewalls and network segmentation gateways often come into play. Learn more about ICS security from CISA.
- Implementing Zero Trust Architectures: Microsegmentation is a cornerstone of Zero Trust security models.By enforcing strict authentication and authorization for every user and device trying to access any resource, regardless of their location, organizations can significantly enhance their security posture.
Every connection is treated as untrusted until explicitly verified. Explore NIST’s Zero Trust Architecture.
Implementing a Network Segmentation Strategy
Implementing network segmentation requires careful planning and execution. 🗺️
It’s not a task to be taken lightly, but the benefits far outweigh the effort.
1. Assess Your Current Network
Before you begin, gain a deep understanding of your existing network infrastructure, data flows, and asset criticality. 🧐
Identify sensitive data, critical applications, and potential vulnerabilities.
2. Define Segmentation Zones
Based on your assessment, define logical segmentation zones.
These could be based on business units, application tiers (web, application, database), data sensitivity, or user roles.
3. Design Your Segmentation Architecture
Choose the appropriate segmentation technologies (VLANs, firewalls, microsegmentation platforms, SDN) that align with your requirements and budget.
Map out how traffic will flow between segments and define your security policies.
Consider a phased approach, starting with less critical segments and gradually expanding.
4. Implement and Test
Carefully implement your segmentation strategy, ensuring that all devices and applications continue to function as expected.
Thorough testing is crucial to identify and resolve any connectivity issues or unintended access restrictions.
5. Monitor and Maintain
Network segmentation is not a set-it-and-forget-it solution. 🔄
Continuously monitor your network for suspicious activity and regularly review and update your segmentation policies to adapt to evolving threats and business needs.
Automated tools can assist in this ongoing process. Find more insights on network segmentation implementation.
Challenges and Considerations
While the benefits of network segmentation are immense, organizations should be aware of potential challenges: 🚧
- Complexity: Large-scale segmentation can increase network complexity, requiring skilled personnel for design, implementation, and management. Gartner offers insights into network complexity.
- Initial Investment: Implementing advanced segmentation, especially microsegmentation or SDN, may require significant upfront investment in technology and training.
- Application Dependencies: Understanding and mapping all application dependencies is critical to avoid breaking essential services when implementing segmentation policies.
- Policy Management: Managing a large number of granular security policies across many segments can be challenging without proper automation and tooling.
The Future of Network Segmentation
The landscape of network security is constantly evolving, and so too is network segmentation. 🔮
We are seeing a continued shift towards more dynamic, automated, and identity-aware segmentation.
The integration of artificial intelligence and machine learning (AI/ML) will play an increasingly important role in identifying traffic patterns, detecting anomalies, and suggesting optimal segmentation policies.
Furthermore, as hybrid and multi-cloud environments become the norm, seamless segmentation across on-premises data centers and various cloud providers will be a key focus.
The goal is to achieve ubiquitous security that adapts to the fluid nature of modern IT infrastructures. Explore future trends in network security with Cloudflare.
“The only way to do great work is to love what you do.”
– Steve Jobs
Conclusion
Network segmentation is no longer an advanced luxury but a fundamental requirement for any organization serious about cybersecurity and operational resilience. 💯
By logically dividing your network, you create robust internal defenses that drastically limit the impact of breaches, enhance compliance, and improve overall network performance.
While it presents certain complexities, the long-term benefits in terms of reduced risk and increased security posture are undeniable.
Embracing network segmentation, particularly microsegmentation and zero-trust principles, is a critical step towards building a truly resilient and secure digital environment in the face of ever-growing cyber threats. 🌐
